IT outsourcing has evolved from a cost-cutting tactic into a strategic growth engine for modern organizations. Whether you’re scaling a product team, accelerating a roadmap, or filling critical skill gaps, outsourcing now offers a level of flexibility, expertise, and operational efficiency that sometimes traditional hiring simply can’t match.
And the shift is only accelerating. Post-pandemic research from Deloitte analysts reveals a lasting shift in how companies establish and manage distributed teams. Trust, productivity, and delivery no longer depend on being in the same room—they depend on the right model, the right governance, and the right partner. As a result, CEOs, CTOs, and PMs are increasingly using outsourcing not just to reduce costs, but to innovate faster, manage risk, and secure a competitive advantage.
If you’re evaluating outsourcing for your next initiative, this guide will help you choose the best-fit model. We break down the strengths and trade-offs of each approach, explain when each model delivers the most value, and provide a decision process to help you align your project’s scope, budget, and ambitions with the right outsourcing strategy.
TL;DR
- The IT outsourcing model defines how businesses work with external vendors. There are 8 main types of outsourcing models that businesses can choose from:
- By Location: Onshore outsourcing model, nearshore outsourcing model, offshore outsourcing model
- By Pricing: Fixed-Price Model, Time and Material Model (T&M)
- By Engagement: Delicate team model, IT Staff Augmentation Model, Project-Based Model
- The choice of outsourcing model has a significant impact on your delivery timeline, costs, and ongoing operational strength. Match your project scope, schedule, and required control to the model—onshore, nearshore, offshore, fixed-price, time-and-materials (T&M), or dedicated teams—for favorable results in terms of time, budget, and quality.
- Work with a partner who turns strategy into outcomes, not just code. Sunbytes supports CEOs, CTOs, and PMs with flexible engagement models, security-by-design capabilities, and scalable workforce solutions, helping you accelerate delivery while reducing operational risk. Explore how Sunbytes can strengthen your next IT outsourcing initiative.
What is the IT Outsourcing Model? Why Outsourcing Model Selection is the Crucial Success Factor
An IT outsourcing model defines how businesses work with external vendors, including the level of control retained, responsibilities transferred, and how risks, costs, and workloads are shared.
Selecting the right model has a direct impact on project outcomes, technical quality, and long-term business resilience. A misaligned model can delay delivery, increase costs, or limit innovation, while the right choice accelerates your roadmap and provides access to specialized talent.

Main types of IT Outsourcing Models
There are three main types of IT outsourcing models: location-based, pricing-based, and engagement-based, as follows:
By Location:
Onshore outsourcing model
- Operational Mechanics: Onshore development means partnering with IT vendors in the same country. Shared legal environments, business norms, and time zones facilitate straightforward collaboration.
- Pros: Onshore model offers high cultural alignment, strong language proficiency, and simplified compliance, making it ideal for complex, security-sensitive, or highly regulated projects.
- Cons: Onshore rates are typically the highest, and companies in regions such as the US, UK, or Western Europe may incur significantly greater development costs compared to other models.
Nearshore outsourcing model
- Operational Mechanics: Nearshore development involves collaborating with third-party teams in nearby or neighboring countries, typically within the same or adjacent time zones.
- Pros: Nearshore solutions strike a strategic middle ground, offering better cost efficiency compared to onshore vendors while preserving much of the cultural fit and scheduling convenience. Shared regional norms also minimize misunderstandings in requirements and stakeholder expectations.
- Cons: On the downside, although more affordable than onshore, nearshore rates can still exceed offshore pricing, and the talent pool, while strong, may be smaller.
Offshore outsourcing model
- Operational Mechanics: Offshore development assigns projects to teams in distant countries, often across significant time zone differences. This model typically uses a “follow-the-sun” workflow, where offshore teams progress work outside the home team’s working hours, accelerating delivery cycles.
- Pros: Offshore outsourcing delivers the strongest cost advantages and access to a global, highly diverse talent pool – making it a preferred model for fast-growing companies and innovation-driven projects
- Cons: However, geographic distance can introduce communication delays, cultural nuances, and additional management overhead. Without structured processes and clear alignment, these challenges may impact quality or timelines.
By Pricing:
Fixed-Price Model
- Operational Mechanics: The Fixed-Price model establishes a predetermined scope, timeline, and budget before development begins. Vendors commit to delivering a defined set of features for an agreed cost, making planning straightforward and minimizing financial uncertainty. This model works best when requirements are stable, documentation is clear, and the project vision is unlikely to change.
- Pros: Its greatest advantage is predictability—executives gain clarity over costs and deadlines, which simplifies budgeting and stakeholder reporting
- Cons: However, fixed pricing limits flexibility, which leads to any changes to scope requiring renegotiation, potentially slowing down progress
Time & Materials (T&M) Model
- Operational Mechanics: The time and materials model bills clients for actual hours worked, resources used, and materials consumed.
- Pros: Its flexibility supports dynamic projects, complex integrations, and long-term development cycles where scope may evolve. Companies benefit from real-time visibility into progress and can scale resources up or down as needed
- Cons: Cost predictability is lower than with fixed-price models, so strong project oversight is needed to prevent budget overruns.
By Engagement Type:
Dedicated Team Model
- Operational Mechanics: The dedicated team model provides a long-term, full-time team working exclusively on your product, acting as an extension of your in-house department. The vendor manages hiring and administration, while your leadership retains strategic control.
- Pros: This model delivers strong continuity, deep product understanding, and predictable capacity—ideal for ongoing development pipelines or scaling digital initiatives
- Cons: Productivity depends on your internal management, and the augmented team usually does not take ownership of outcomes.
IT Staff Augmentation Model
- Operational Mechanics: Staff augmentation involves adding external engineers or specialists to your internal team as needed. These professionals work under your processes and leadership to fill resource gaps.
- Pros: The key advantage is agility, you can rapidly fill skill gaps, boost delivery speed, or handle peak workloads without committing to long-term hires.
- Cons: The downside is that productivity depends heavily on your internal management capacity, and the augmented team does not typically take ownership of outcomes.
Project-based model
- Operational Mechanics: Project-Based model assigns full responsibility for delivery to the vendor, who manages planning, development, quality assurance, and timelines from start to finish. Companies define objectives and requirements upfront, and the vendor executes the project independently with minimal day-to-day oversight required from the client
- Pros: This model offers convenience and clarity, making it ideal for well-scoped, short- to mid-term projects. Companies benefit from hands-off execution and predictable milestones.
- Cons: Limited flexibility may hinder adaptation to changing requirements, and project success depends heavily on the accuracy and completeness of initial documentation. This model is less suitable for fast-changing or highly innovative environments.
Quick Comparison Table
| Model | Cost/Pricing | Setup Speed | Scalability | Risk Level | Best Use Case |
| Onshore | High cost | Fast | Moderate | Low | Regulated industries, complex projects requiring close collaboration |
| Nearshore | Moderate | Fast | High | Medium | Needing real-time communication with reduced cost |
| Offshore | Low cost | Moderate | Very high | Medium–High | Long-term development, cost-sensitive projects, access to large tech talent pools |
| Model | Cost/Pricing | Setup Speed | Scalability | Risk Level | Best Use Case |
| Fixed-Price Model | Predictable, fixed budget | Slow–Moderate (requires clear scope) | Low | Medium | Small to mid-sized projects with well-defined requirements |
| Time & Materials (T&M) Model | Flexible, hourly-based | Fast | High | Medium | Projects with evolving scope, Agile development, innovation-driven builds |
| Dedicated Team Model | Monthly cost | Moderate | Very high | Low–Medium | Continuous product development, scaling up |
| IT Staff Augmentation | Pay per engineer | Fast | High | Medium | Filling skill gaps quickly, boosting an internal team temporarily |
| Project based | Fixed or mixed pricing | Moderate | Low–Moderate | Medium–High | One-off, clearly scoped projects. Vendor handles end-to-end delivery |
How to choose the right IT outsourcing model
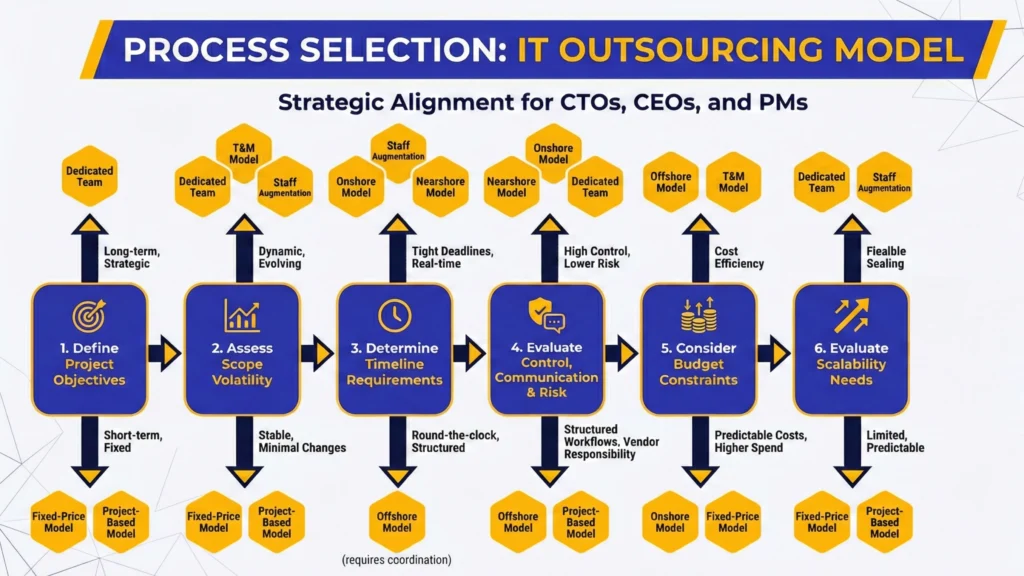
Selecting the right IT outsourcing model is a strategic decision that can directly impact project outcomes, cost efficiency, and long-term business resilience. CTOs, CEOs, and project managers must carefully align their project requirements with the most suitable model, considering factors such as scope, timeline, budget, control, and scalability. Below is a structured approach to guide this decision.
Matching Your Project Needs to the Right Model
Define Your Project Objectives:
Start by clearly outlining the goals of your project. Are you developing a new product, enhancing an existing system, or undertaking a one-time initiative? Understanding your objectives helps determine what model will suit you most.
- Strategic, long-term initiatives may benefit from a Dedicated Team.
- While short-term, fixed deliverables often align with Fixed-Price or Project-Based models.
Assess Scope Volatility
Assess the likelihood of your project requirements changing during the development process.
- T&M Model handles dynamic and innovative projects where requirements may frequently change.
- The Dedicated Team Model is suitable for evolving workloads that need ongoing adjustments.
- Staff Augmentation Model allows quick adaptation to new tasks or skill gaps.
- Projects with stable requirements and minimal changes are better suited for the Fixed-Price Model or the Project-Based Model, as these models reduce scope-related risks.
Determine Timeline Requirements
Consider the urgency of your delivery schedule:
- Staff Augmentation Model enables rapid onboarding to meet tight deadlines.
- Onshore Model and the Nearshore Model provide real-time collaboration for projects requiring immediate attention.
- Offshore Model offers round-the-clock development, but time zone differences require careful coordination and structured processes for effective delivery.
Evaluate Control, Communication, and Risk Tolerance
Decide how much oversight you require and how comfortable your team is managing distributed vendors
- The Onshore Model and Nearshore Model offer higher control, easier communication, and lower risk.
- Offshore Model demands structured workflows and clear reporting to mitigate geographic and cultural challenges.
- Dedicated Team Model grants strategic and operational oversight, while the Project-Based Model transfers most responsibility to the vendor.
Risk-averse executives may prefer models that maximize governance, such as Onshore, Nearshore, or Dedicated Teams.
Consider Budget Constraints
- Offshore Model and T&M Model typically offer the highest cost efficiency.
- Onshore Model and Fixed-Price Model involve higher expenditures but can provide predictable costs and lower risk for complex projects.
Evaluate Scalability Needs
Assess whether your project may require scaling up or down resources.
- For projects with evolving workloads, Dedicated Teams and Staff Augmentation offer flexible scalability without the burden of internal recruitment.
- Fixed-Price and Project-Based models offer limited scalability but provide predictability for projects with stable scope and requirements.
CTOs, CEOs, and PMs can utilize this structured evaluation to align project characteristics with the optimal outsourcing model, thereby maximizing cost efficiency, quality, and delivery speed while minimizing risk.
Future-Proofing Your Outsourcing Strategy (2026 & Beyond)
The Rise of Hybrid Teams: Leveraging Global and Local Talent Pools
Hybrid teams combine onshore expertise with offshore development, striking a balance between cost control, local market knowledge, and customer proximity.
Typical configurations include product managers or designers located near the business while offshore developers handle implementation. Security-sensitive components may be kept onshore, while standard features are developed offshore.
Success requires clear responsibility boundaries. Define which decisions need local approval and which can be handled offshore. Establish overlapping hours for real-time collaboration and utilize asynchronous communication to leverage time zones to your advantage.
Integrating AI/ML: Outsourcing for Innovation, not just Execution
AI-assisted development accelerates delivery by using AI tools for code generation, automated testing, documentation, and problem discovery. Vendors who integrate AI into their workflows can deliver faster without sacrificing quality.
Ask vendors specific questions, such as which AI tools they use, how AI-generated code is validated, and what percentage of progress is aided by AI. Vendors who provide clear answers are better positioned to deliver innovation, not just execution.
AI-assisted outsourcing is best for projects with defined needs and repetitive patterns. It is less effective for highly experimental or research-driven projects where AI tools lack sufficient training data.
Security & Compliance by Default: Mandating Global Standard Certifications
Stricter global regulations, such as GDPR in Europe, CCPA in California and , hold organizations accountable for protecting user data. Non-compliance can result in financial penalties, reputational damage, and loss of customer trust. For outsourced development, security is now a core business requirement.
“Secure before coding” is the new standard. Security should be integrated into the development lifecycle from the start, ensuring data privacy, access controls, encryption, and auditability in every module. The rise in cyberattacks, stricter regulations, and higher customer expectations makes security essential for business resilience and trust.
Select vendors with ISO, SOC 2, GDPR, or other relevant certifications to ensure compliance with global standards and regulations. Clearly define security protocols in SLAs and implement monitoring for ongoing compliance. Certified teams mitigate regulatory risk and instill confidence in sensitive projects, making security a non-negotiable foundation for success.

Best Practices for your Digital Project
Establishing Clear KPIs and SLAs ensures alignment between your organization and the outsourcing partner, providing measurable benchmarks for delivery, quality, and performance.
Starting small with a pilot project allows you to validate processes, team dynamics, and vendor capabilities before scaling to larger initiatives.
Regular communication, through status updates, sprint reviews, and executive checkpoints, maintains transparency, prevents misalignment, and accelerates the resolution of issues.
Mandating security protocols, quality standards, and IP protection from day one safeguards sensitive data and ensures compliance with industry regulations while maintaining software integrity.
Planning for knowledge transfer and off-boarding ensures continuity, preserves institutional knowledge, and minimizes disruption when team members transition or projects evolve.
Take The Next Step Toward Innovation!
Choosing the right IT outsourcing model is only the first step—executing it effectively requires a partner who can translate strategy into results. Sunbytes helps CEOs, CTOs, and project leaders turn IT initiatives into measurable business outcomes by combining deep delivery expertise, proven methodologies, and scalable talent solutions.
Whether your goal is to accelerate software development, optimize operational workflows, or secure sensitive systems, Sunbytes provides integrated services that ensure your outsourcing strategy is not only implemented but future-proofed, efficient, and aligned with business priorities.
About Sunbytes
Sunbytes is a comprehensive one-stop partner to scale your business. Our mission is to turn business leaders’ strategic ambitions into delivered outcomes—fast, measurable, and de-risked. We have designed our solutions into three main pillars: Transform – Secure – Accelerate. We boost business growth – while reducing risk – by Transforming your Business, Securing it by Design, and Accelerating your operation. We focus on measurable results: clearer scope, fewer overruns, faster time-to-value, and a de-risked path to scale.
A few facts about Sunbytes:
-FD Gazellen Award winner
-12+ years of delivery experience
-300+ projects across diverse industries
-Experience supporting organisations working toward ISO 27001, HIPAA, and other requirements
Our Transform pillar provides flexible, scalable models tailored to your needs. Whether it’s a Dedicated Team, Team-as-a-Service, Dedicated Developers, or Custom Software Development, Sunbytes enables you to scale engineering capacity, optimize workflows, and accelerate product delivery. Our approach ensures that your outsourced teams are fully aligned with your internal processes, KPIs, and strategic priorities, giving CTOs and PMs confidence that initiatives are executed efficiently and effectively.
How our other pillars strengthen Transform
-Cyber Security Solutions: Security-by-design practices (access control, secrets management, automated testing) ensure transformation doesn’t introduce avoidable risk.
– Accelerate Workforce Solutions: When execution capacity is the bottleneck, we provide the right talent and cadence to deliver the roadmap without slowing operations.
Ready to Move Forward?
Contact Sunbytes today to book a FREE Consultation for your IT Outsourcing project
FAQs
1. What should we outsource to vendors?
Outsource activities that are execution-heavy, specialized, or require flexible scalability, such as software development, QA automation, DevOps support, UI/UX design, data engineering, and maintenance. These functions benefit from external expertise, predictable delivery, and cost-efficiency, especially when your internal team needs to focus on strategy, architecture, and core business priorities.
2. What don’t outsource?
Avoid outsourcing activities that define your competitive advantage, contain highly sensitive IP, or involve core business logic that must remain in-house. Strategic decision-making, product vision, security architecture, and proprietary algorithms are best maintained internally. Outsourcing these can create dependency risks and weaken your organization’s core knowledge base.
3. When should we run a security audit or pentest in an outsourced project?
Conduct security audits and penetration tests before any MVP or production launch and after every major architectural or feature change. Start by establishing a secure configuration baseline, including access control, secrets management, infrastructure hardening, and CI/CD security. Then validate it with an adversary-style pentest and a clear remediation roadmap.
To strengthen your security posture, explore Security Audit & Pentest services from Sunbytes Cyber Security services.
Let’s start with Sunbytes
Let us know your requirements for the team and we will contact you right away.


