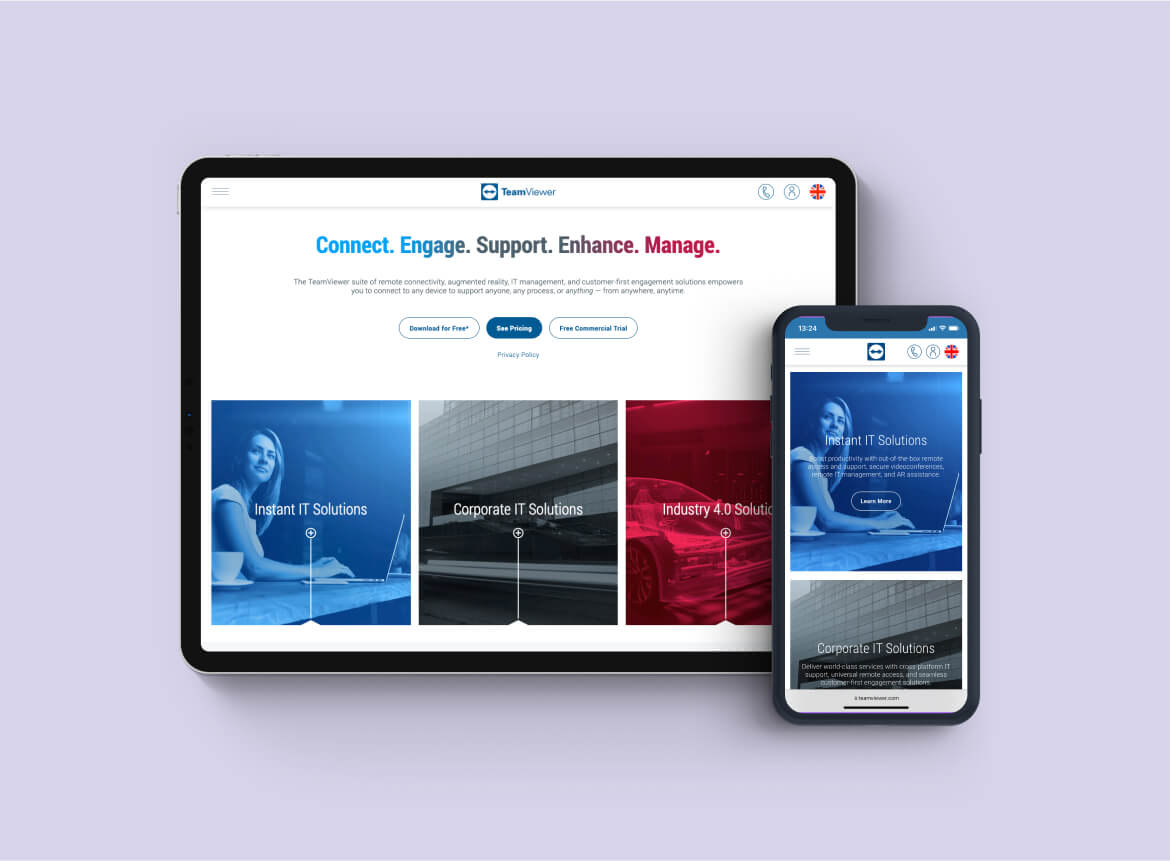
Are we secure?
Get a defensible baseline and a clear roadmap in 3–4 weeks with Sunbytes CyberCheck.
ISO 27001-minded delivery process • GDPR-aware by design • Experience supporting ISO 27001

Not sure if you’re secure?
This page is for teams that need a clear answer fast — not another lengthy checklist.- You can’t answer questionnaires without guessing
- You can’t show evidence when customers ask
- You don’t know what matters most to fix first
- Security work is reactive, not planned
- Ownership is unclear (who does what, when)
- Third-party/vendor risk is hard to explain clearly
What you get with CyberCheck
A fixed-scope package designed to give you clarity, priorities, and proof without slowing down your team.

Baseline snapshot
Prioritised findings
30/60/90-day roadmap
Evidence checklist

Executive summary
How CyberCheck works
Fixed price • Built for lean teams • Minimal disruption

Stage 1: Kickoff & Scope
- Align on context, systems, and expectations
- Confirm scope + timeline + evidence request list
- Output: agreed scope + plan

Stage 2: Review & Validate
- Review provided evidence and validate what’s in place
- Quick clarification with key stakeholders
- Output: findings by domain + gaps/risk notes

Stage 3: Report & Roadmap
- Turn findings into priorities and a practical action plan
- Walkthrough session to align owners.
- Output: baseline report + 30/60/90 roadmap + evidence checklist
What we cover (18 security domains)
A structured view of your security posture — from governance to technical controls and response readiness.
- Governance & Policies — ownership, direction, documentation
- Risk Management — identify, prioritise, track risks
- Asset & Inventory Management — visibility of systems and data
- Security Awareness — reduce human-related risk
- Third-Party & Vendor Risk — assess and manage suppliers
- Identity & Access Management — access control, MFA, JML basics
- Privileged Access — admin boundaries and accountability
- Change & Release Management — controlled, traceable changes
- Endpoint Security — device hygiene and protection
- Network Security — exposure control and segmentation
- Secure Configuration & Hardening — baseline configurations
- Vulnerability Management — find, prioritise, fix
- Logging & Monitoring — visibility, alerting, audit trails
- Application Security — secure SDLC control points
- Endpoint Security — device hygiene and protection
- Network Security — exposure control and segmentation
- Secure Configuration & Hardening — baseline configurations
- Vulnerability Management — find, prioritise, fix
- Logging & Monitoring — visibility, alerting, audit trails
- Application Security — secure SDLC control points
Your outcomes
A structured view of your security posture — from governance to technical controls and response readiness.
Faster, cleaner security responses
Answer questionnaires with consistent wording and reusable proof points.
Clear priorities for your team
Know what to fix first, what can wait, and why, without guesswork.
Stakeholder alignment
Give leadership and delivery teams one shared view of risk and next steps.
What you can confidently answer
After CyberCheck, you can say that:
“Here’s our current posture (with evidence).”
“Here are our top priorities and timeline.”
“Here’s what we’re doing next — and who owns it.”
Choose your next step
Start with clarity. Continue with continuous improvement or compliance support when you’re ready.
Sunbytes Compliance Readiness
When you need structure for audits and compliance milestones.
- Gap closing & control hardening
- Evidence preparation
- Audit-facing documentation support
Sunbytes CyberCheck
When you need Baseline + priorities for lean teams.
- Fixed scope, fixed price
- Minimal disruption
- Clear 30/60/90 roadmap
Sunbytes CyberCare
For teams ready to run a continuous security cycle.
- Ongoing improvements & tracking
- Evidence stays up to date
- Works well after CyberCheck
Not sure where to start? Book a CyberCheck call – we’ll recommend the right path.
Why Sunbytes

14 years of experience
300+ successful projects operation

30K+ highly qualified professional

7+ years of experience of our delicate developers

20+ countries helped
FAQs
CyberCheck is not a full pentest engagement. It’s an evidence-led baseline and prioritisation package. If deeper testing is needed, we’ll recommend the right next step.
Yes, once scope is confirmed. The goal is predictable cost and minimal disruption.
Yes. After CyberCheck, we can support remediation through CyberCare (continuous improvement) or align help based on your capacity and roadmap.
We can work under NDA and follow strict data-minimisation: only request what’s needed, keep access controlled, and avoid pulling unnecessary sensitive information.
CyberCheck helps you identify gaps and priorities against common compliance expectations. It’s not a certification or audit. If you have a specific framework in mind (e.g., ISO 27001), our Cyber Compliance Readiness can help you prepare with the right evidence, controls, and documentation.
Discuss your cybersecurity needs with Sunbytes
Secure your business with expert protection