European organizations are scrutinizing their cybersecurity compliance approach in light of the NIS2 Audits requirement. Board members and executives are especially attuned to the operational upheaval that even a single missed requirement can create. They know that an updated directive means stricter reviews, heavier fines, and a higher risk of reputational setbacks. The time to act is now.
The Rising Tide of Enforcement
Regulatory bodies have raised the bar on oversight for network and information systems. Under NIS2, authorities possess greater power to investigate security breaches and audit an organization’s readiness. Moreover, the directive includes the possibility of 2% of worldwide annual turnover as fines or up to 10 million euros. Financial loss on this scale can cause liquidity nightmares and jeopardize strategic initiatives.
In comparison, earlier iterations of cybersecurity rules focused more on guidance than on enforcement. This time, auditors arrive with sharper tools and the authority to sanction noncompliant entities swiftly. With the average global cost of a data breach reaching $4.35 million, it showcases that unprepared firms risk compounding financial impact beyond the regulatory fine itself.

Penalties Beyond the Bottom Line
Financial penalties are a pressing concern, but they are not the only worry. Publicly disclosed breaches carry a hidden cost that outlasts any immediate settlement. Public sentiment can sour, prospective customers may look elsewhere, and existing partners could question the stability of the relationship.
For instance, a mid-size fintech company might pay a modest penalty for delayed compliance, only to discover that hesitant investors pull back from a new funding round. The financial outlay stretches far beyond the initial fine, and the company’s competitive edge erodes. In extreme cases, operational downtime can result from forced corrective measures. These shutdowns harm revenue generation and staff morale, driving a prolonged recovery timeline.
Public Fallout and Operational Disruption
Data leaks tied to an audit failure can trigger intense media scrutiny. Accounts of user data or patient records winding up on dark web forums tend to dominate headlines for weeks. Once stakeholders see headlines referencing lost data, trust dissolves. Without trust, a well-established name in healthcare or e-commerce may spend years trying to recapture its former reputation.
Even a relatively small incident can snowball. The moment a vulnerability is exploited or reported, organizations scramble to plug security holes. This response often involves expensive short-term solutions, such as:
- Emergency contracts with cybersecurity consultants
- Extra overtime for IT teams
- Reallocation of budgets initially intended for other growth-focused projects.
These expenses, layered on top of potential regulatory fines, explain why reactive measures quickly eclipse the cost of proactive actions.
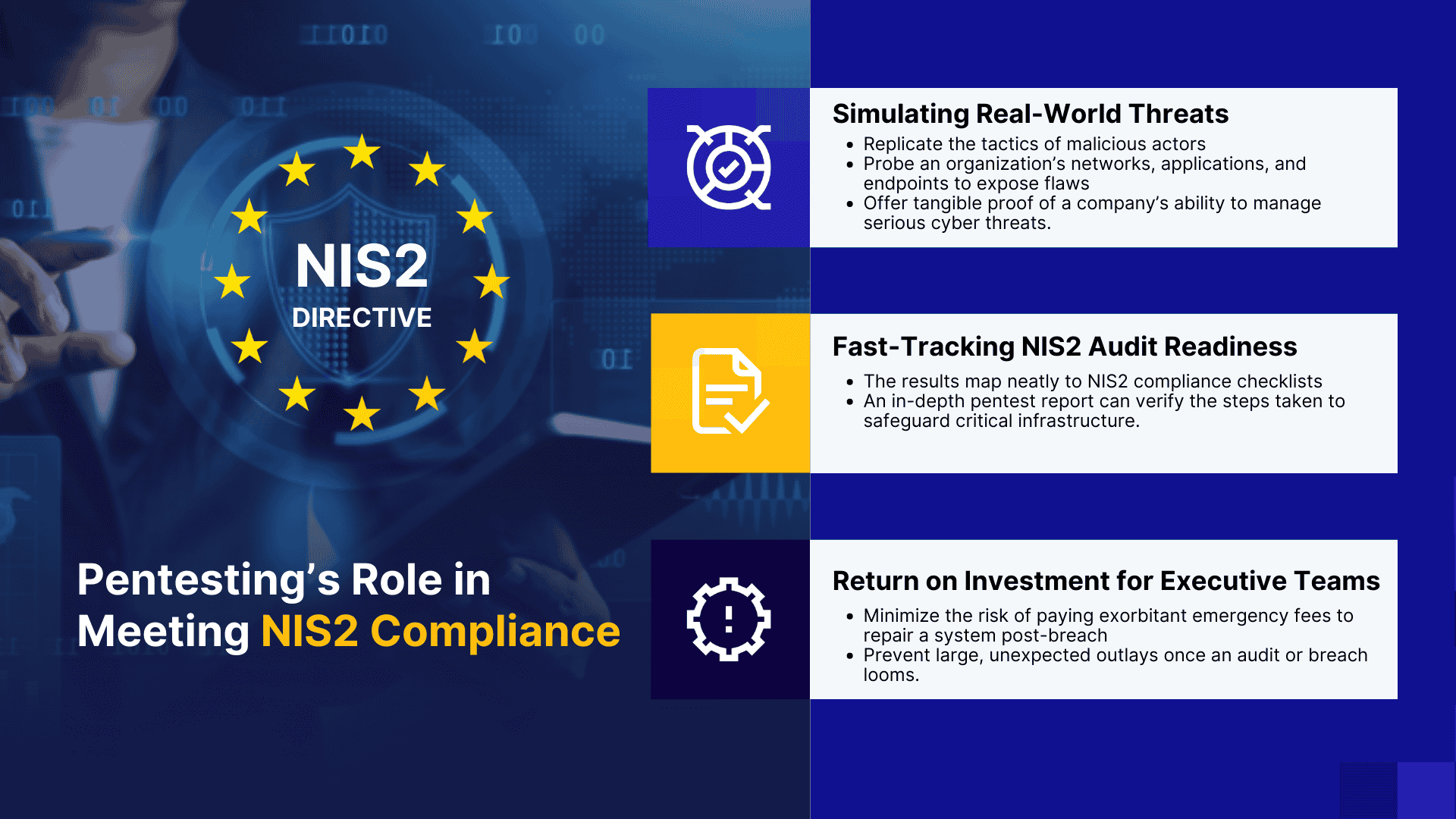
Pentesting’s Role in Meeting NIS2 Compliance Objectives
Simulating real-world threats
A penetration test goes beyond automated scans or checkbox compliance exercises. It replicates the tactics of malicious actors, probing an organization’s networks, applications, and endpoints to expose flaws. Once these weaknesses become visible, security teams can address them before they turn into disruptive incidents. By showing that your company has vigorously tested its systems, you bolster your position in any NIS2 audit scenario.
Penetration testing also offers clarity that mere vulnerability scans cannot match. While scans might highlight superficial misconfigurations, a simulated attack reveals how sophisticated or persistent aggressors could sidestep existing defenses. In doing so, it offers tangible proof of a company’s ability to manage serious cyber threats.
Read more: The complete guide to penetration testing for businesses
Fast-tracking NIS2 audit readiness
C-level executives find penetration tests particularly valuable because the results map neatly to NIS2 compliance checklists. When auditors request documentation of secure configurations, an in-depth pentest report can verify the steps taken to safeguard critical infrastructure.
A real-world illustration: a midsize manufacturing firm needed rapid certification for its industrial control systems. Instead of sifting through disparate technical logs, the company presented a structured pentest report demonstrating that each flaw had been patched or isolated. The audit concluded swiftly, saving both time and administrative expense.
Return on Investment for executive teams
Proactive testing yields a tangible financial upside. By uncovering vulnerabilities early, organizations minimize the risk of paying exorbitant emergency fees to repair a system post-breach. There is also less chance of business interruption, a factor that could damage quarterly earnings or long-term profitability.
Another overlooked benefit is stakeholder confidence. When boards see that executives have prioritized robust assessments, they view the overall leadership as forward-thinking. A small, scheduled investment in cyber defenses often prevents large, unexpected outlays once an audit or breach looms.
Why Executive Oversight Matters
Cybersecurity as a strategic pillar
Management can no longer treat cybersecurity as an afterthought. It deserves regular attention at board meetings and formal inclusion in overarching business strategies. A dedicated committee, reporting directly to leadership, ensures that budgets, policies, and partnerships revolve around safeguarding digital assets. This strategic stance fosters a culture where employees and third parties understand the significance of data protection, ultimately reducing the likelihood of breaches.
Building stakeholder trust
Investors and partners expect transparency when it comes to safeguarding shared data. Regularly scheduled updates on pentesting activities, patch deployments, and broader security measures soothe concerns about potential disruptions. People do business with entities they perceive as reliable. Showing a consistent commitment to security can tip the scales in favor of landing contracts or attracting new funding.
Forward-thinking executives often share high-level findings, such as the number of vulnerabilities fixed or the average time to patch, without revealing sensitive technical details. This method of disclosure showcases accountability and fosters reassurance among clients or regulators.
Incorporating pentesting into corporate strategy
One productive approach involves scheduling penetration tests before a major product rollout or infrastructure upgrade. Conducting them in parallel with development cycles ensures that security controls receive the same attention as usability or functionality.
Budgeting becomes smoother when executives allocate funds specifically for these assessments each year. Treat this expenditure as an ongoing operational priority rather than a periodic cost. Making cybersecurity an embedded element of strategic planning reduces the need for sudden, large-scale financial outlays when NIS2 audit deadlines arrive.
Navigating NIS2 Audits with Expert Insights
Partner with Sunbytes to pinpoint vulnerabilities and safeguard your organization’s infrastructure before regulators step in. Our expertise fortifies your cybersecurity posture in alignment with NIS2 Audit expectations, minimizing risks and maximizing stakeholder confidence.
Let’s start with Sunbytes
Let us know your requirements for the team and we will contact you right away.


