“Why do I need this?” or “What even is penetration testing?” are common questions from business owners when they first hear about it. In 2024, the average cost of a data breach reached $4.88 million, and 2023 saw a sharp increase in cyberattacks, affecting more than 343 million victims. The numbers are alarming. Many businesses, especially in niche industries like healthcare and fintech, might not have the technical knowledge to realize they need this service to protect against breaches. Others struggle with fixing existing vulnerabilities in their code, wasting valuable time and resources that could be better spent on core activities. Therefore, you need a comprehensive penetration testing guide, crafted by experts
If these challenges sound familiar, our penetration testing guide could be the solution your business needs. Let’s explore how this technique can help strengthen your security and safeguard your assets.
What is Penetration Testing (Pen Testing)?
Penetration testing, often called “pen-testing,” is a simulated cyber attack against your system to uncover vulnerabilities and identify weak spots in your applications, networks, and overall infrastructure that could be exploited by hackers. Think of it as a fire drill for your cybersecurity defenses.
A penetration test involves ethical hackers who use the same tools and techniques as cybercriminals to try and breach your defenses.
This process provides invaluable insights into your security posture, revealing not just obvious weaknesses but also the hidden flaws that could lead to a significant breach.
Why is Penetration Testing MORE than just a “Nice-to-Have”?
You might wonder, “Is this necessary for my business?” The short answer is yes, and why? To uncover vulnerabilities before the real threats do. This isn’t about pointing fingers or adding unnecessary complexity to your operations; it’s about understanding where the cracks are in your defenses so you can fortify them.
Cyber threats are evolving, and so should your defenses
93% of organizations had two or more identity-related breaches in 2023. Cybercriminals are always looking for new ways to exploit weaknesses. Whether it’s through sophisticated phishing attacks, exploiting software vulnerabilities, or leveraging social engineering tactics, their methods are constantly evolving.
Penetration testing allows you to stay one step ahead by regularly identifying and fixing vulnerabilities in your systems. It’s like a continuous check-up for your cybersecurity health.
Data breaches can be devastating
A data breach isn’t just a technical issue—it’s a business nightmare. The average cost of a data breach in 2024 is $4.88 million, and the impact goes far beyond just financial loss.
In the wake of a cyber attack, it’s not just your data that’s at risk—it’s your reputation. You risk losing customer trust, facing legal consequences, and suffering long-term damage to your brand’s reputation.
Compliance and legal protection
Many industries are governed by strict regulations when it comes to data protection. From GDPR to HIPAA, compliance isn’t optional.
Regular penetration testing can help you meet these regulatory requirements, avoiding hefty fines and legal repercussions. It also demonstrates to stakeholders that you’re committed to protecting sensitive information.
Strengthening your defenses
Even the most robust security systems have weaknesses. Penetration testing provides a thorough evaluation of your defenses, highlighting areas that need improvement.
This allows your IT team to focus on strengthening your security measures, whether it’s patching software vulnerabilities, improving network security, or tightening access controls.
What are the Types of Penetration Testing?
Different penetration tests focus on various attack vectors and environments, providing a comprehensive security evaluation.
Web penetration testing
Web application penetration testing simulates real-world attacks to identify security vulnerabilities within web applications. This includes testing for common vulnerabilities like cross-site scripting (XSS), SQL injection, and broken authentication, as well as identifying misconfigurations and business logic flaws.
A successful attack against a web application can lead to data breaches, financial losses, reputational damage, and compliance violations. Web pentesting helps businesses proactively identify and mitigate these risks.
API Pentesting
API penetration testing focuses on identifying security vulnerabilities in Application Programming Interfaces (APIs). APIs allow different software systems to communicate and exchange data. API pentesting simulates attacks to uncover authorization, authentication, input validation, and data exposure weaknesses.
APIs are increasingly used to connect critical business systems and share sensitive data. Vulnerabilities in APIs can expose businesses to significant risks, including data breaches, financial fraud, and service disruptions.
Mobile application penetration testing
With more than 6.3 billion smartphone users globally, it’s clear why the mobile app industry is booming. With the rise of mobile apps, ensuring their security is crucial.
Mobile application penetration testing assesses the security of mobile apps on platforms like Android and iOS. It involves testing for vulnerabilities related to data storage, network communication, authentication, authorization, and reverse engineering.
Mobile apps often handle sensitive user data and connect to critical backend systems. Mobile app pentesting helps protect user data and ensure the integrity of mobile services.

Number of smartphone mobile network subscriptions worldwide from 2016 to 2023, with forecasts from 2023 to 2028 – Source: Statista
Cloud penetration testing
As more businesses migrate to the cloud, with 94% of companies adopting cloud computing in their operations in the US, securing cloud infrastructure is vital.
Cloud security penetration testing assesses the security of cloud environments and infrastructure. It involves identifying misconfigurations, vulnerabilities in cloud services, and weaknesses in access controls, data protection, and network security. Cloud pentesting helps ensure that cloud deployments are secure, compliant, and protected against attacks.

Source: Edge Delta
Red teaming
Red teaming simulates real-world, advanced cyberattacks to test an organization’s defenses. It goes beyond traditional pentesting by employing a wider range of tactics and techniques, including social engineering, physical intrusion attempts, and sophisticated exploitation methods.
Red teaming provides a comprehensive assessment of an organization’s security posture and its ability to detect and respond to advanced threats. It helps identify weaknesses in people, processes, and technologies.
Penetration Testing vs. Vulnerability Assessment
Although both methods hunt for weaknesses, they serve different roles within a broader security strategy.
Vulnerability Assessment
- Automated Scans: Tools like Nessus or OpenVAS produce extensive lists of potential weaknesses.
- Baseline Reporting: Offers a snapshot of system posture but lacks the deeper understanding that exploitation attempts provide.
- Frequency: Often scheduled more frequently to maintain a running tally of possible entry points.
Penetration Testing
- Realistic Exploitation: Ethical hackers chain vulnerabilities to illustrate tangible threats, such as data extraction or system takeover.
- Detailed Remediation Roadmap: Findings go beyond identification, highlighting specific solutions and best practices to avoid similar pitfalls.
- Value for Executive Decision-Makers: C-level leaders and compliance officers benefit from witnessing how an attacker might escalate privileges or access sensitive material in real-world scenarios.
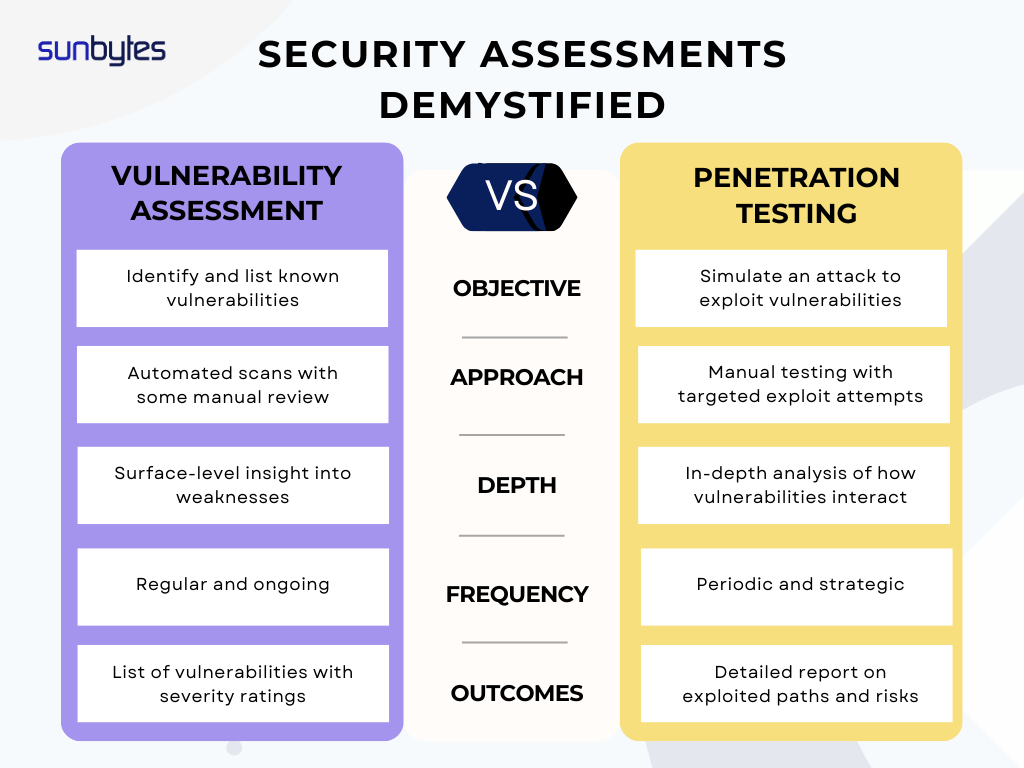
Companies often commence with a vulnerability assessment before committing to an in-depth penetration testing engagement. Over time, testing intervals depend on regulatory demands, system updates, and the complexity of new deployments.
The Process of Penetration Testing Guide
A methodical penetration testing procedure locates hidden fault lines in your digital infrastructure. Ethical hackers adopt real adversarial methods to ensure they capture realistic vulnerabilities. Businesses then gain meaningful data for ongoing remediation and operational resilience.
Stage 1: Planning and Scoping
Projects start by clarifying which domains, networks, or applications the pen testers will analyze. This scope details any specific techniques, like social engineering or physical intrusion attempts that the testers can or cannot use. An agreed-upon scope preserves transparency and prevents disruptions to critical services.
Step 2: Reconnaissance and Information Gathering
The initial reconnaissance phase forms the foundation of the entire penetration testing process. During this critical stage, testers gather intelligence about the target system, including IP addresses, domain information, network services, mail servers, and network topology. This phase utilizes open-source intelligence (OSINT) and publicly accessible sources to collect additional details about the in-scope environment
Key Activities Include:
- Collecting publicly available information about the target organization
- Identifying network infrastructure and system architecture
- Mapping domain structures and subdomains
- Gathering employee information through social media and professional networks
Step 3: Vulnerability Identification
The scanning phase involves a thorough technical examination of the target system using specialized tools. Port scanners, vulnerability scanning software, and network mappers are employed to assess how the target application behaves in different scenarios and identify potential vulnerabilities. This discovery scanning tests for perimeter vulnerabilities and determines available ports and services for targeted hosts.
Essential Scanning Activities:
- Port scanning to identify open services and potential entry points
- Vulnerability scanning using automated tools like Nessus
- Network mapping to understand system architecture
- Service enumeration to identify running applications and versions
Step 4: Exploitation
During the exploitation phase, penetration testers attempt to exploit the vulnerable areas identified within the scope of the test. This phase allows testers and organizations to verify the severity of weaknesses identified within the systems. Testers use various strategies such as SQL injection, cross-site scripting (XSS), and backdoor attacks to identify ways to bypass firewalls and breach systems.
Exploitation Techniques Include:
- Testing identified vulnerabilities for exploitability
- Attempting to gain unauthorized access to systems
- Extracting sensitive data to demonstrate impact
- Documenting successful exploitation methods and their severity
Step 5: Reporting and Post-Test Strategy
This final stage produces a comprehensive report detailing discovered exposures, their severity, and actionable fixes. Each vulnerability is accompanied by a recommended remediation roadmap, often referencing CVSS (Common Vulnerability Scoring System) values for prioritization. A qualified pentest provider places significant emphasis on ongoing consultancy rather than a quick exit:
- Tailored guidance: Beyond disclosing issues, the consultancy team helps create a plan to address root causes. This includes advice on patch management, policy updates, or user awareness training.
- Continuous support: A pass from a single pen test does not guarantee permanent protection. Experts keep a close watch on emerging threats and share insights with your in-house teams or other stakeholders.
Select the Right Penetration Testing Tools
Automated Scanning Tools
Utilize automated scanners such as Nessus or Burp Suite for swift identification of common vulnerabilities, which saves significant time during the assessment process. These tools provide baseline vulnerability identification and help prioritize manual testing efforts.
Manual Testing Tools
Apply specialized manual testing tools such as Metasploit for vulnerabilities that require human expertise to properly exploit. Manual testing is essential for identifying complex vulnerabilities that automated tools might miss.
Specialized Application Tools
Use specialized tools created for specific testing scenarios, such as OWASP ZAP for web application testing2. Ensure selected tools are compatible with your current architecture for a smooth testing process.
What Constitutes a “Qualified” Pentest Under NIS2, ISO, and MIAUW
Certain regulations and frameworks, NIS2, ISO, and the Dutch MIAUW frameworks, specify criteria that define a legitimate penetration testing procedure. Meeting these benchmarks demonstrates a proactive approach to cybersecurity and often satisfies compliance requirements for legal audits or industry accreditations.
What is the ISO 27001 Pentest?
An ISO 27001 pentest is a targeted penetration test designed to assess your organization’s defenses against potential threats. Also called a hack test, it uncovers vulnerabilities and weak points within your digital ecosystem. After examining the findings, you can bolster your information security to minimize risks. If you’re seeking ISO 27001 certification, our specialized penetration tests support you in meeting the benchmark for best practices.
By conducting an ISO 27001 pentest, you gain insight into where your organization stands in terms of cybersecurity. Key advantages include:
- Reduced Security Incidents: Pinpointing vulnerabilities helps you address them before they become full-blown security breaches.
- Enhanced Protection for Critical Data: A thorough pentest confirms that sensitive information, such as customer details and corporate IP, remains secure.
- Comprehensive Weakness Identification: Testing reveals areas that need improvement, ensuring you can tackle issues proactively.
- Actionable Recommendations: Our detailed reports outline practical steps to strengthen your defense mechanisms.
- Compliance with Standard A12.6: Adhering to requirement A12.6 of the ISO 27001 framework is simpler when you have concrete pentest results.
While both an ISO 27001 audit and an ISO 27001 pentest aim to uphold high security standards, they differ in scope:
ISO 27001 Audit
An audit evaluates your Information Security Management System (ISMS) to verify if it aligns with ISO 27001 requirements.
ISO 27001 Pentest
A pentest takes a deeper, technical look at your infrastructure to pinpoint real-world vulnerabilities. Its findings can be used to bolster the evidence you present during an ISO 27001 audit.
When combined, these two processes offer a holistic method for improving and maintaining top-tier security measures within your organization.
What is the NIS2 Pentest?
A NIS2 pentest is a simulated cyberattack on a target system, intended to uncover vulnerabilities before malicious actors can exploit them. By starting with pentesting now, you can fortify your security measures and prepare for the upcoming NIS2 requirements.
Whether the NIS2 Directive applies to your organization depends on various factors, including the industry in which you operate and the size of your organization. It is important to note that NIS2 affects both essential and important entities, meaning a wide range of organizations could be covered by the directive.

Pentesting plays a critical role under NIS2. NIS2 requires organizations to conduct regular pentests as part of their cyber risk management. This ensures that your security measures remain current and effective against the latest cyberthreats. In addition, NIS2 places a strong emphasis on active cyber protection, staff training, and boosting awareness of cybersecurity risks.
Learn why C-suits should embrace NIS2 early.
What is the MIAUW-Compliant Pentesting?
MIAUW, the Methodology for Information Security Research with Audit Value, was developed and adopted by the Dutch government. This framework ensures consistent, high-standard results. By using MIAUW, you can guarantee uniform, comparable, and auditable pentest outcomes, addressing the inconsistencies of previous methods and offering clear insights into the true security of your systems.
MIAUW is an open-source methodology and is freely available for anyone to use. Whether you are a decision-maker, a CISO, or a cybersecurity professional, MIAUW offers a concrete and reliable way to better control risks.
Download our free checklist to ensure your penetration tests comply with the MIAUW framework.
Pentesting Approaches: Black Box, Grey Box, and White Box
The depth of system knowledge testers receive significantly alters the style and scope of penetration testing.
- Black Box Testing: Testers approach the environment as external attackers with minimal data about the system. The aim is to see how effectively public-facing defenses stand up against a direct assault.
- Grey Box Testing: The business grants partial access, such as user credentials, high-level architecture, or other internal information, to testers. This middle-ground perspective often reveals vulnerabilities overlooked by external-only scanning.
- White Box Testing: Pen testers receive full intelligence on source code, database schemas, and network topologies. White box methods are the most exhaustive and can uncover subtle coding flaws or advanced misconfigurations that black box or grey box methods might miss.
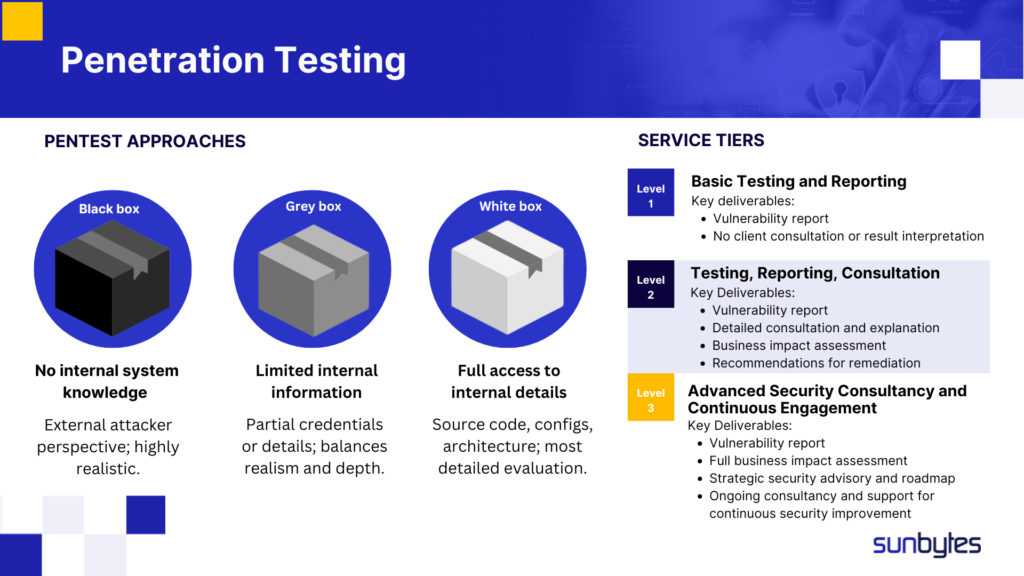
Selecting the right approach depends on your objectives. For instance, black box testing validates external boundary strength, while white box testing verifies the integrity of critical workflows or specialized internal tools. Learn how Sunbytes uses the black box method to help our clients launch their products successfully.
Make Penetration Testing Part of Your Security Strategy
At Sunbytes, our certified team goes beyond simple reports. We collaborate continuously, offer tailored remediation, and help you stay adaptive in a shifting cyber realm.
If you’re looking for clarity on which approach to pen testing best suits your environment or you want practical advice on addressing findings, contact us to discuss your next steps.
Frequently Asked Questions
enetration testing, often called “pen-testing,” is a simulated cyber attack against your system to uncover vulnerabilities and identify weak spots in your applications, networks, and overall infrastructure that could be exploited by hackers. Think of it as a fire drill for your cybersecurity defenses. With the average cost of a data breach reaching $4.88 million in 2024 and 343 million victims affected by cyberattacks in 2023, penetration testing helps you identify and fix vulnerabilities before real threats exploit them.
A penetration test involves ethical hackers who use the same tools and techniques as cybercriminals to try and breach your defenses. This process provides invaluable insights into your security posture, revealing not just obvious weaknesses but also hidden flaws that could lead to a significant breach. The testing simulates real-world attack scenarios to give you a comprehensive understanding of your security vulnerabilities
There are several types of penetration testing, each focusing on different attack vectors:
-
Web penetration testing: Identifies vulnerabilities in web applications like cross-site scripting (XSS), SQL injection, and broken authentication
-
API pentesting: Focuses on security vulnerabilities in Application Programming Interfaces, testing for authorization, authentication, and data exposure weaknesses
-
Mobile application penetration testing: Assesses security of mobile apps on Android and iOS platforms, testing data storage, network communication, and authentication
-
Cloud penetration testing: Evaluates cloud environments and infrastructure security, identifying misconfigurations and access control weaknesses
-
Red teaming: Simulates advanced cyberattacks using social engineering, physical intrusion attempts, and sophisticated exploitation methods
The penetration testing process follows five key stages:
-
Planning and Scoping: Clarifying which domains, networks, or applications will be analyzed and defining testing boundaries
-
Reconnaissance and Information Gathering: Building a blueprint of the target environment through public resources and digital footprint analysis
-
Vulnerability Identification: Using automated tools and manual probing to detect weaknesses like neglected patches or exposed databases
-
Exploitation: Testing which vulnerabilities can actually be exploited to measure real impact
-
Reporting and Post-Test Strategy: Producing comprehensive reports with severity ratings, actionable fixes, and ongoing consultancy support
The three approaches differ in the level of system knowledge provided to testers:
-
Black Box Testing: Testers approach as external attackers with minimal system knowledge, validating external boundary strength
-
Grey Box Testing: Testers receive partial access like user credentials or high-level architecture, revealing vulnerabilities overlooked by external-only scanning
-
White Box Testing: Testers get full intelligence on source code, database schemas, and network topologies for the most exhaustive testing
Testing frequency depends on several factors including regulatory demands, system updates, and deployment complexity. Companies often start with vulnerability assessments before committing to in-depth penetration testing engagements. Regular testing is recommended, especially after significant system changes or as required by compliance frameworks like NIS2


