This guide explains how to move from “we want ISO 27001” to “we are audit-ready” with clear steps, expected deliverables, and typical timing for SMEs.
TL;DR
The ISO 27001 certification process has 8 practical stages: planning, ISMS scope, risk assessment, control implementation, training, evidence collection, certification audit, and continuous improvement. Most SMEs need structured preparation to pass efficiently—especially around documentation quality, risk treatment, and audit readiness.
The ISO 27001 certification process in 8 practical steps
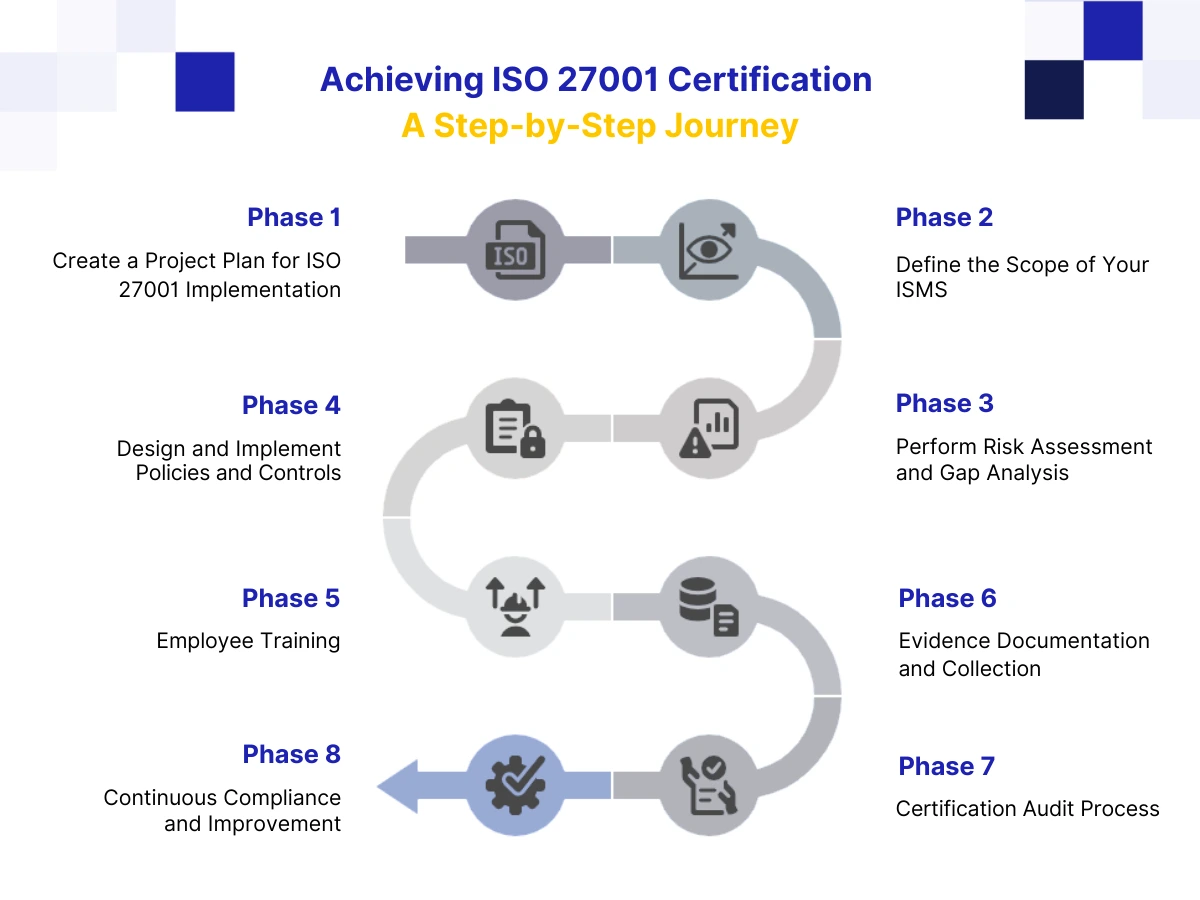
Set governance and implementation ownership
Define who owns the program, who approves risk decisions, and who runs day-to-day execution.
- Key output: program owner + RACI
- Typical pitfall: unclear ownership across IT, legal, HR, and operations
Define ISMS scope
Decide which entities, systems, and business processes are in-scope.
- Key output: ISMS scope statement
- Typical pitfall: scope too broad too early, or too narrow to satisfy customer/legal requirements
Run a formal risk assessment and gap analysis
Identify threats, vulnerabilities, business impact, and existing control gaps.
- Key output: risk register + gap report
- Typical pitfall: generic risk descriptions with no business context
Build risk treatment plan and implement controls
Prioritize controls and assign owners, deadlines, and acceptance criteria.
- Key output: Statement of Applicability (SoA) + Risk Treatment Plan
- Typical pitfall: control list exists, but implementation evidence is weak
Train employees and operational teams
Turn policies into behavior through role-based training.
- Key output: training plan + attendance and effectiveness records
- Typical pitfall: one-off awareness sessions with no reinforcement
Collect audit-ready evidence
Organize proof that controls are designed and operating effectively.
- Key output: evidence library mapped to controls
- Typical pitfall: scattered evidence, no versioning, missing logs/approvals
Complete certification audit (Stage 1 + Stage 2)
Work with an accredited certification body to validate design and operation.
- Key output: audit findings + corrective actions + certification decision
- Typical pitfall: unresolved nonconformities before deadlines
Maintain certification through continuous compliance
Operate internal audits, corrective actions, and management reviews on a recurring cycle.
- Key output: maintenance plan for surveillance and recertification
- Typical pitfall: “project mindset” instead of ongoing operating model
ISO 27001 audit stages explained
Stage 1: Documentation and design review
Auditors assess whether your ISMS framework is adequately designed for certification.
Stage 2: Effectiveness audit
Auditors verify whether controls are implemented and working in practice.
Stage 3: Surveillance audits
Periodic checks during the certification cycle to confirm ongoing compliance.
Stage 4: Recertification audit
Full reassessment at the end of the certification cycle.

Employee Cybersecurity Training Session
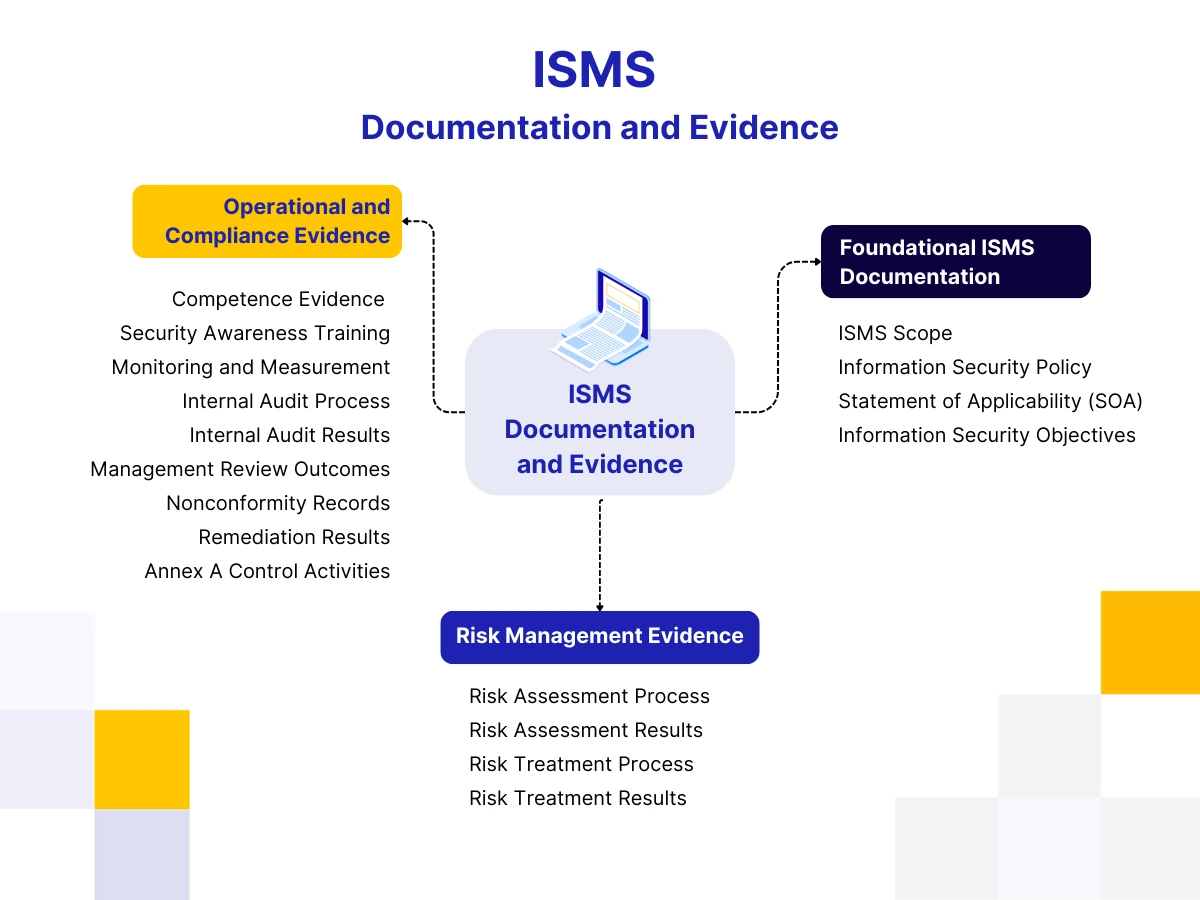
Required evidence checklist (SME version)
Foundational ISMS documentation
- ISMS scope
- Information security policy set
- Roles and responsibilities
- Internal audit and management review records
Risk management evidence
- Risk assessment methodology
- Risk register
- Risk treatment plan
- Statement of Applicability (SoA)
Operational compliance evidence
- Access control and permission records
- Incident management records
- Vendor/security reviews
- Backup/recovery test records
- Training completion and awareness logs
Typical SME timeline: what to expect
Fast-track (mature teams): 4–6 months
- Existing controls already running
- Strong documentation culture
- Dedicated internal owner
Standard path: 6–12 months
- Most SMEs fall here
- Mix of control implementation + process stabilization
Extended path: 12+ months
- Limited ownership capacity
- Incomplete documentation discipline
- Multiple entities/processes in scope from day one
Why ISO 27001 projects slow down (and how to avoid it)
Most delays are not caused by the standard itself—they come from execution gaps:
- Undefined scope and shifting priorities
- Weak evidence governance
- Unclear risk ownership
- Training treated as “check-the-box”
- Late corrective action handling before audit
Build in-house vs partner-led preparation
Use in-house-only when you have:
- Internal ISO 27001 implementation experience
- Available cross-functional capacity
- Strong policy + evidence discipline
Use partner-led support when you need:
- Faster audit readiness
- Clear prioritization and implementation roadmap
- Hands-on execution support across teams
How we helps with Sunbytes Compliance Readiness
Sunbytes supports SMEs with a practical model built for execution, not just documentation.
- ISO 27001 readiness assessment and gap mapping
- Prioritized remediation roadmap with ownership
- Policy/control alignment and evidence structure
- Audit preparation support (Stage 1 / Stage 2)
- Continuous improvement setup for surveillance cycles
Sunbytes is headquartered in the Netherlands and works with a Transform – Secure – Accelerate approach:
- Transform: secure architecture and engineering practices reduce control gaps early
- Secure: structured compliance implementation and audit readiness
- Accelerate: scalable team and delivery support keeps compliance from slowing growth
Explore: Sunbytes Compliance Readiness
Frequently Asked Questions
Most SMEs complete preparation and certification within 6–12 months, depending on scope complexity, internal ownership, and evidence maturity.
Implementation is building and operating your ISMS. Certification is the external audit validation by an accredited body.
Common issues include weak evidence traceability, inconsistent control operation, and unresolved corrective actions.
Yes. Even with external support, internal ownership is essential for approvals, operational changes, and long-term maintenance.
No. Certification must be maintained through surveillance audits and periodic recertification.
Yes. Sunbytes can support readiness assessment, remediation planning, control/evidence preparation, and audit preparation.
Let’s start with Sunbytes
Let us know your requirements for the team and we will contact you right away.


