A DevSecOps pipeline integrates automated security testing and policy enforcement directly into every stage of the CI/CD workflow, enabling teams to identify and fix vulnerabilities without slowing software delivery. This approach transforms security from a bottleneck into an accelerator by embedding protective measures throughout development, testing, and deployment phases.
Modern software teams face mounting pressure to release features faster while maintaining bulletproof security. Traditional approaches that treat security as a final gate create dangerous delays and expensive remediation cycles. DevSecOps pipelines solve this challenge by making security everyone’s responsibility and automating protective measures from code commit to production monitoring.
What Is a DevSecOps Pipeline?
A DevSecOps pipeline is a continuous integration and continuous delivery (CI/CD) workflow that embeds security practices, automated testing, and compliance checks into every phase of software development and deployment. Unlike traditional DevOps pipelines that add security as an afterthought, DevSecOps treats security as a first-class citizen throughout the entire software lifecycle.
The fundamental difference lies in the “shift-left” philosophy – moving security considerations earlier in the development process rather than relegating them to pre-production testing. This approach transforms security from a reactive bottleneck into a proactive enabler that accelerates delivery by catching issues when they’re cheapest and easiest to fix.
Key characteristics of the DevSecOps pipeline include:
- Automated security scanning at multiple pipeline stages
- Policy-as-code enforcement for compliance and governance
- Continuous monitoring that extends into production environments
- Shared responsibility model where developers own security outcomes
- Fast feedback loops that provide actionable security insights within minutes
DevSecOps pipeline typically orchestrates security tools like Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), Software Composition Analysis (SCA), and Infrastructure as Code (IaC) scanning. These tools run automatically based on triggers like code commits, pull requests, or deployment events, ensuring a consistent security posture without manual intervention.
Why DevSecOps Matters in 2025
The software landscape has fundamentally shifted, making DevSecOps beneficial and essential for competitive advantage.
- Faster release cycles (hundreds of times daily vs. monthly/quarterly) create more security vulnerabilities.
- Economic pressure makes fixing vulnerabilities in production 100x more expensive than in development, forcing tough choices: delay or ship vulnerable code.
- Stricter regulations (SOC 2, PCI DSS, AI governance) demand continuous security validation, making automated DevSecOps essential.
- Supply chain attacks (SolarWired, Log4j) highlight the need for automated scanning and attestation within DevSecOps for third-party dependencies and SBOM accuracy.
- Cybersecurity talent shortage means organizations can’t hire enough specialists, making automated DevSecOps testing the only scalable security solution.
Organizations implementing mature DevSecOps practices gain significant competitive advantages: faster time-to-market, lower security remediation costs, improved compliance posture, and enhanced customer trust through demonstrable security commitments.
Read more: Navigate the maze of EU cybersecurity compliance in 2 minutes
Core Phases of a DevSecOps Pipeline
A DevSecOps pipeline comprises interconnected phases that embed security practices throughout the software development lifecycle. Each phase includes specific security gates, automated tools, and validation checkpoints that ensure vulnerabilities are caught and addressed before they reach production.
| Phase | Security Activities | Typical Tools | Key Security Gate |
| Planning & Threat Modeling | – Threat modeling workshops – Security requirements definition – Risk assessment and prioritization – Compliance target setting | – IriusRisk – ThreatModeler – Jira Software – Slack | Risk catalogue approved and security plan signed off |
| Source Code Management | – Secret scanning for exposed credentials – Pre-commit security hooks – Code review integration – Branch protection policies | – Git with security plugins – GitHub Advanced Security – GitLab- Bitbucket | Secret scan passes with no exposed API keys or passwords |
| Continuous Integration | – Static Application Security Testing (SAST) – Software Composition Analysis (SCA) – Unit security tests – Binary analysis and integrity checks | – SonarQube- Checkmarx – Snyk – OWASP Dependency-Check – Jenkins with security plugins | Build fails on critical CVEs or OWASP Top 10 violations |
| Testing & Validation | – Dynamic Application Security Testing (DAST) – Interactive Application Security Testing (IAST) – API security testing – Infrastructure scanning | – OWASP ZAP – IBM AppScan – Burp Suite – Nessus – Qualys | Security monitoring alerts are configured, and incident response procedures are tested |
| Release & Deployment | – Infrastructure as Code (IaC) scanning – Container image security validation – Configuration management audits – Principle of least privilege enforcement | – HashiCorp Terraform – Docker security scanning – Ansible – Kubernetes admission controllers – AWS Config | Image scan clean and configuration compliance verified |
| Monitoring & Response | – Runtime application self-protection – Security information and event management – Anomaly detection – Incident response automation | – Splunk – Datadog Security – Falco – AWS GuardDuty – Prometheus with security metrics | Security monitoring alerts are configured, and incident response proceduresare tested |
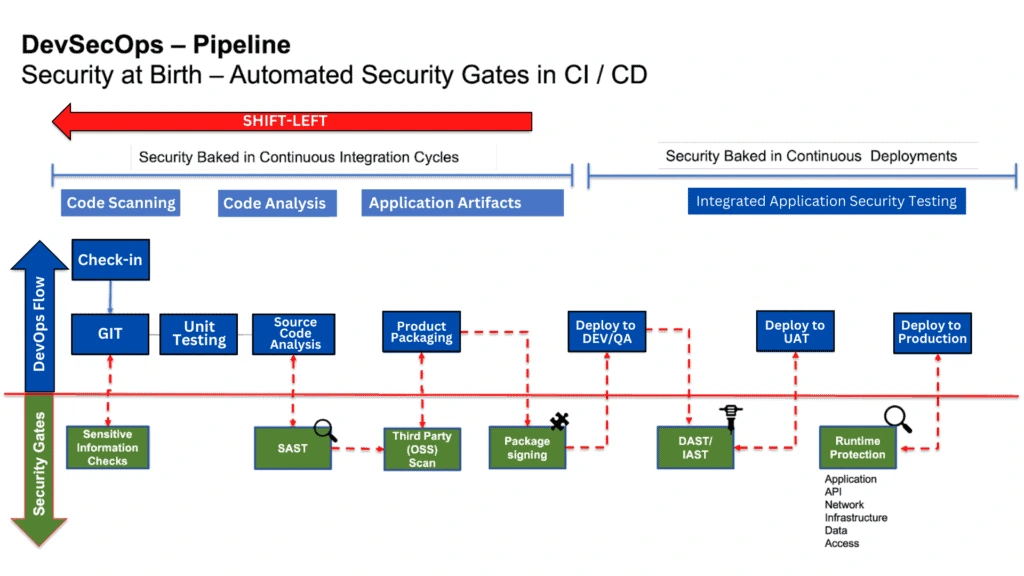
Source: K21 Academy
10 Best Practices for a Secure & Fast DevSecOps Pipeline
Implementing a DevSecOps pipeline successfully requires balancing security rigor with delivery velocity. These proven best practices enable teams to maintain a robust security posture while accelerating software delivery through intelligent automation and cultural transformation.
Shift Security Left with Strategic Automation
Integrate security testing directly into developer workflows through IDE plugins, pre-commit hooks, and automated code analysis. Deploy Static Application Security Testing (SAST) scanners that examine source code for vulnerabilities like SQL injection and cross-site scripting before code reaches shared repositories. However, avoid scanning entire codebases daily; instead, focus SAST scans on incremental code changes to prevent information overload and maintain pipeline speed.
Configure pre-commit hooks to catch hardcoded secrets, API keys, and credentials before they enter version control systems. This prevents sensitive data exposure while providing immediate feedback to developers during their natural workflow.
Implement Intelligent Automated Security Testing
Deploy comprehensive automated security testing across multiple pipeline stages, including SAST for source code analysis, Dynamic Application Security Testing (DAST) for runtime vulnerability detection, and Software Composition Analysis (SCA) for dependency scanning. Use DAST continuously since it’s designed to provide real-time results during application runtime, while being selective with SAST to avoid overwhelming teams with excessive alerts.
Integrate tools like SonarQube, OWASP ZAP, and Snyk directly into CI/CD pipelines to provide fast feedback without manual intervention. Configure smart alerting features that prioritize critical vulnerabilities and reduce false positives to prevent alert fatigue that can impact developer productivity.
Treat Security and Compliance as Code
Adopt Infrastructure as Code (IaC) practices to manage security configurations as versioned, auditable code files. This approach ensures consistent security settings across environments while enabling rapid rollbacks and configuration tracking. Use tools like Terraform, Ansible, and Puppet to codify security policies and automatically enforce compliance standards.
Implement declarative compliance checks using tools like OpenSCAP or InSpec to validate systems against policy definitions. This enables automated auditing and reduces configuration drift that can create security gaps across different environments.
Secure Container Images and Runtime Environments
Implement comprehensive container security by scanning base images for vulnerabilities, using minimal container images to reduce attack surface, and enforcing image signing for supply chain integrity. Deploy Kubernetes admission controllers and policy engines like Open Policy Agent (OPA) to enforce security policies at deployment time.
Configure runtime protection through tools like Falco that monitor container behavior for anomalous activities and potential security breaches. This “shift-right” approach complements early-stage security testing by providing continuous protection in production environments.
Centralize Secrets Management at Scale
Deploy centralized secrets management solutions like HashiCorp Vault or AWS Secrets Manager to eliminate hardcoded credentials throughout your codebase. Integrate these tools directly into CI/CD pipelines to enable dynamic, secure handling of sensitive data without manual intervention.
Implement role-based access controls and secret rotation policies to minimize exposure windows. Configure automated secret scanning in source code repositories to catch accidentally committed credentials before they reach production systems.
Establish Security Champions Within Development Teams
Appoint security champions within each development team to serve as liaisons between developers and security experts. These champions promote faster adoption of security practices and ensure someone on each team understands security vulnerabilities and mitigation strategies.
Provide security champions with specialized training and direct access to security tools and expertise. This distributed model scales security knowledge across the organization while maintaining development team autonomy and velocity.
Create Effective Feedback Loops and Metrics
Establish feedback mechanisms that provide actionable security insights directly to developers in real-time. Move beyond simple automated alerts to deliver contextual information that helps developers understand vulnerability impact and remediation steps.
Implement security metrics that track meaningful outcomes like mean time to remediation, vulnerability escape rates, and security test coverage. Use these metrics to continuously refine security processes and demonstrate security program effectiveness to stakeholders.
Adopt Immutable Infrastructure for Consistency
Implement immutable infrastructure practices where deployed environments cannot be altered after creation. When changes are needed, deploy entirely new versions rather than modifying existing systems. This approach eliminates configuration drift and reduces potential attack vectors.
Use container orchestration platforms and infrastructure automation tools to enable rapid, consistent deployments of immutable infrastructure. This practice ensures that security configurations remain consistent and any unauthorized changes are immediately detectable.
Make Threat Modeling a Continuous Practice
Transform threat modeling from a one-time activity into an ongoing, lightweight practice integrated into agile development cycles. Conduct threat modeling workshops during sprint planning to identify potential attack vectors and security requirements before writing code.
Use tools like IriusRisk or ThreatModeler to systematically analyze application architecture and identify security risks. Update threat models as applications evolve, ensuring that security considerations keep pace with feature development and architectural changes.
Extend Security Testing into Production
Implement “shift-right” security practices by testing security controls in production environments through chaos engineering and continuous monitoring. Deploy runtime application self-protection (RASP) tools and security information and event management (SIEM) systems to detect and respond to threats in real-time.
Conduct regular penetration testing and bug bounty programs to identify vulnerabilities that automated tools might miss. Use production monitoring data to validate that security controls function effectively under real-world conditions and attack scenarios.
Success requires gradual implementation, starting with practices that offer the highest security impact with minimal friction, then expanding coverage as teams develop DevSecOps maturity.
DevSecOps Common Pitfalls & How to Avoid Them
Even well-intentioned DevSecOps pipeline implementations can stumble due to predictable organizational and technical challenges. Understanding these common pitfalls enables teams to proactively address obstacles before they derail security transformation efforts.
“Security as the Team of No” Culture
The most damaging pitfall occurs when security teams position themselves as gatekeepers who primarily reject deployments rather than enablers who facilitate secure delivery. This adversarial dynamic creates friction between development and security teams, leading to workarounds, delayed releases, and ultimately a weaker security posture as developers bypass security controls to meet deadlines.
Remedy:
- Transform security into a collaborative partnership through cross-functional ownership models.
- Embed security champions within development teams who understand both security requirements and delivery pressures.
- Establish shared success metrics that reward teams for both delivery velocity and security outcomes.
Tool Overload and Integration Chaos
Organizations frequently fall into the trap of accumulating multiple security tools without strategic integration, creating a fragmented landscape where tools don’t communicate effectively and generate overwhelming amounts of unactionable alerts. This tool sprawl leads to alert fatigue, inconsistent security coverage, and maintenance overhead that slows pipeline execution.
Remedy:
- Curate a lightweight, integrated security toolchain based on specific organizational needs rather than adopting every available tool.
- Conduct regular audits to eliminate redundant tools and standardize on platforms that offer native integrations with existing CI/CD infrastructure.
- Prioritize tools that provide APIs and automation capabilities over those requiring manual intervention.
False-Positive Fatigue and Alert Overload
When security scanning tools generate excessive false positives or fail to prioritize vulnerabilities effectively, development teams become desensitized to security alerts and may ignore legitimate threats. This phenomenon is particularly problematic with older codebases, where automated scans can identify thousands of low-priority issues that overwhelm development capacity.
Remedy:
- Implement intelligent triage dashboards that prioritize critical vulnerabilities based on exploitability, business impact, and environmental context.
- Establish service level agreements (SLAs) for different vulnerability categories, ensuring that teams focus on high-impact issues first.
- Configure scanning tools to suppress known false positives and tune detection rules based on application-specific contexts to improve signal-to-noise ratios.
Unrealistic Expectations and Implementation Fatigue
Many organizations expect immediate results from DevSecOps implementations, leading to disappointment when cultural and technical transformations require sustained effort over months or years. This impatience often results in abandoned initiatives or superficial implementations that fail to deliver meaningful security improvements.
Remedy:
- Set realistic interim targets and celebrate incremental progress rather than expecting comprehensive transformation overnight.
- Implement DevSecOps practices gradually, starting with high-impact, low-friction changes that demonstrate value quickly.
- Use storytelling techniques to communicate security improvements as user stories that highlight business benefits and stakeholder value.
Top-Down Mandates Without Cultural Foundation
DevSecOps cannot be successfully implemented through executive mandates alone – it requires genuine cultural change that embraces security as a shared responsibility. When leadership attempts to decree DevSecOps adoption without addressing underlying cultural barriers, teams often comply superficially while maintaining existing practices that undermine security objectives.
Remedy:
- Invest in continuous change management that addresses cultural factors through training, awareness programs, and structural adjustments that support collaborative security practices.
- Provide teams with the tools, training, and authority needed to make security decisions within their domains.
- Document role changes and establish clear expectations that help teams understand their expanded security responsibilities.
Exclusive Focus on Code Analysis Without Runtime Protection
Many organizations concentrate exclusively on static code analysis and pre-deployment security testing while neglecting runtime protection and production monitoring. This narrow focus leaves applications vulnerable to novel attacks, configuration drift, and threats that emerge after deployment.
Remedy:
- Implement comprehensive security coverage across the entire application lifecycle, including RASP, web application firewalls, and continuous monitoring systems.
- Deploy tools like microgateway solutions to provide additional defense layers against unknown attack vectors.
- Maintain development team autonomy over application logic.
Inadequate Feedback Loops and Learning Mechanisms
Without effective feedback mechanisms, teams cannot learn from security incidents or improve their DevSecOps pipeline over time. This leads to repeated mistakes, missed opportunities for process improvement, and gradual degradation of security practices as teams lose sight of security outcomes.
Remedy:
- Establish continuous feedback loops that provide actionable insights directly to development teams in real-time.
- Implement security metrics that track meaningful outcomes like mean time to remediation and vulnerability escape rates.
- Conduct regular retrospectives that examine both successful security practices and areas for improvement, creating a learning culture that continuously evolves security capabilities.
Recommended Toolchain for DevSecOps Pipeline (2025 Stack)
Building an effective DevSecOps pipeline requires carefully selected tools that integrate seamlessly across the software development lifecycle. The following toolchain represents the most mature and widely adopted solutions for 2025, chosen for their automation capabilities, developer experience, and enterprise-grade security features.
Planning & Threat Modeling
Primary: IriusRisk provides comprehensive threat modeling capabilities with automated risk assessment and integration into agile workflows. The platform enables teams to conduct lightweight threat modeling sessions during sprint planning while maintaining detailed security documentation.
Alternative: ThreatModeler offers visual threat modeling with automated report generation and compliance mapping. Both tools integrate with popular project management platforms like Jira to ensure security requirements flow directly into development backlogs.
Source Code Management & Early Detection
Primary: GitHub Advanced Security (GHAS) delivers native SAST scanning through CodeQL, automated secret detection, and dependency vulnerability analysis directly within GitHub workflows. This integration provides immediate feedback to developers without context switching between tools.
Alternative: GitLab Ultimate provides an all-in-one platform that covers the entire DevOps lifecycle, featuring natively integrated security scanning, including SAST, DAST, and SCA, within its CI/CD framework. GitLab’s strength lies in its unified approach, which eliminates the complexity of tool integration.
Continuous Integration Security
Primary: SonarQube remains the gold standard for continuous code quality inspection and static analysis, with excellent IDE integration and CI pipeline automation. Its developer-centric approach ensures high adoption rates while maintaining comprehensive security coverage.
Secondary Tools:
- Semgrep for multi-language code security with fast, customizable rule engines
- Snyk Code for developer-first SAST scanning with superior accuracy and reduced false positives
- Checkmarx One for enterprise-grade application security testing with AI-enhanced vulnerability prioritization
Container & Infrastructure Security
Primary: Trivy provides comprehensive container image scanning, Kubernetes configuration analysis, and Infrastructure as Code (IaC) security validation. Its lightweight design and extensive vulnerability database make it ideal for automated pipeline integration.
Complementary Tools:
- Aqua Security for runtime protection and multi-cloud security posture management
- KICS for Infrastructure as Code scanning with support for Terraform, CloudFormation, and Kubernetes manifests
- Open Policy Agent (OPA) for policy-as-code enforcement in Kubernetes environments
Dynamic Testing & Runtime Protection
Primary: OWASP ZAP offers robust open-source dynamic application security testing with active vulnerability scanning and passive traffic monitoring. Its proxy-based architecture provides comprehensive coverage for web applications and APIs.
Enterprise Alternative: Veracode delivers enterprise-grade DAST capabilities with low false-positive rates under 5% and scalable scanning for hundreds of applications simultaneously. The platform excels in protected pre-production environments where comprehensive testing is critical.
Secrets Management & Access Control
Primary: HashiCorp Vault provides industry-leading secrets management with dynamic secret generation, fine-grained access controls, and comprehensive audit logging. Its encryption-as-a-service capabilities enable secure data handling without application code modifications.
Integration: Vault integrates seamlessly with CI/CD pipelines through native APIs and supports multiple authentication backends, including Kubernetes, cloud IAM, and LDAP systems.
Monitoring & Observability
Primary: Prometheus with Grafana delivers comprehensive metrics collection and visualization for security monitoring. This combination provides real-time insights into application security posture and enables custom alerting for security events.
Complementary Tools:
- Falco for runtime security monitoring in Kubernetes environments with real-time threat detection
- Splunk for security information and event management (SIEM) with advanced analytics capabilities
Orchestration & Integration Platform
Unified Platform: Jit streamlines DevSecOps by centralizing 17 robust security tools, including Prowler, KICS, Nancy, npm-audit, Trivy, and ZAP into a single orchestrated toolchain. This approach reduces tool sprawl while maintaining comprehensive security coverage across the entire pipeline.
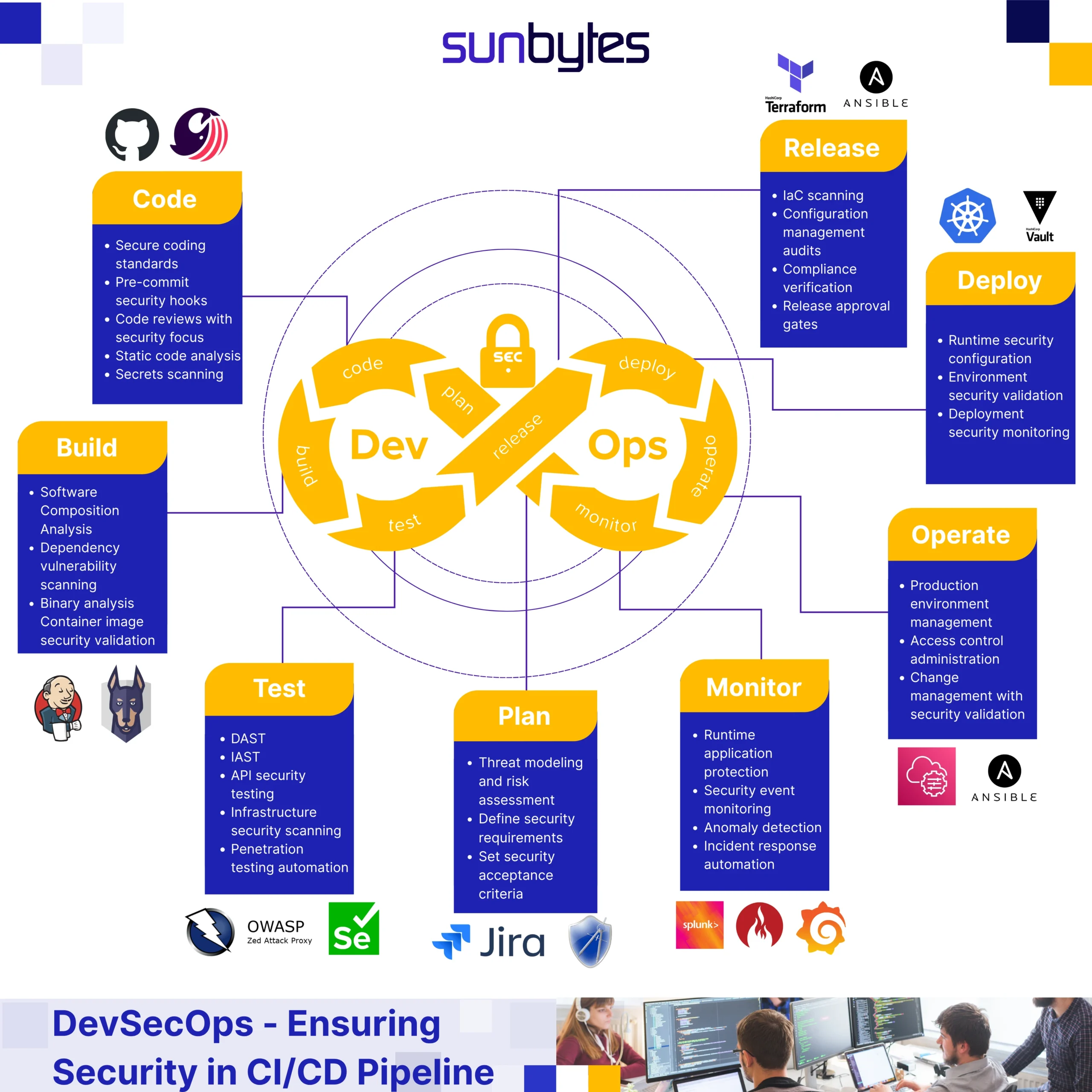
DevSecOps Pipeline Implementation Strategy
Start with core tools that provide immediate value: GitHub Advanced Security or GitLab Ultimate for source code management, SonarQube for CI integration, and Trivy for container scanning. These foundational tools establish security practices without overwhelming development teams.
Gradually expand coverage by adding specialized tools like HashiCorp Vault for secrets management and OWASP ZAP for dynamic testing. This phased approach ensures teams can adapt to new security practices while maintaining delivery velocity.
Prioritize integration over feature completeness when selecting tools. Choose solutions that offer robust APIs, webhook support, and native CI/CD integrations to minimize manual overhead and ensure consistent security enforcement across all development activities.
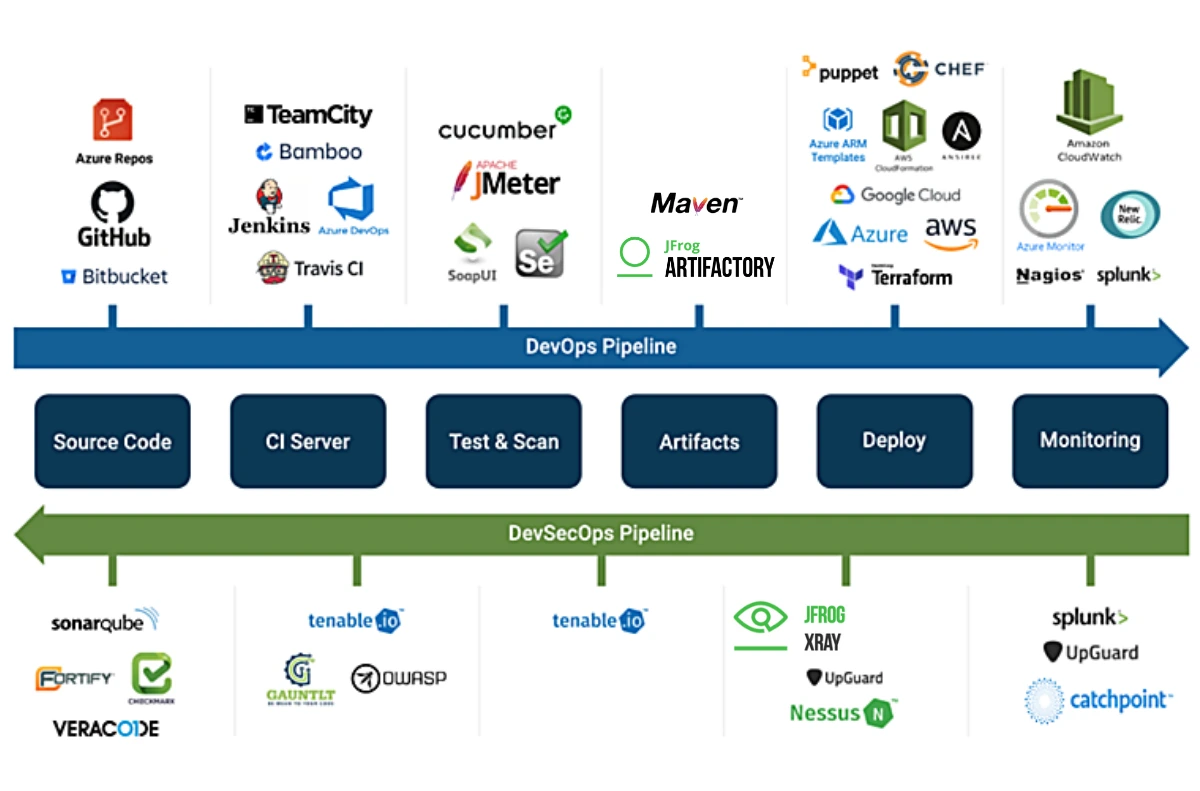
Source: DevOps
Quick-Start DevSecOps Pipeline Template
Getting started with DevSecOps doesn’t require complex configurations or extensive tool integration. This quick-start template provides a foundational pipeline that implements essential security scanning stages in a logical progression, enabling teams to begin securing their CI/CD workflows immediately.
GitLab CI/CD DevSecOps Pipeline Template
The following YAML configuration demonstrates a complete DevSecOps pipeline that progresses through Static Application Security Testing (SAST), Software Composition Analysis (SCA), and Dynamic Application Security Testing (DAST). This staged approach ensures comprehensive security coverage while maintaining clear separation of concerns.
# .gitlab-ci.yml - Complete DevSecOps Pipeline Template
stages:
- build
- test
- security
- deploy
variables:
# Configure your application URL for DAST scanning
DAST_WEBSITE: "https://your-staging-app.com"
# Enable/disable specific security scans
SAST_DISABLED: "false"
DEPENDENCY_SCANNING_DISABLED: "false"
DAST_DISABLED: "false"
# Include GitLab's built-in security templates
include:
- template: Security/SAST.gitlab-ci.yml
- template: Security/Dependency-Scanning.gitlab-ci.yml
- template: Security/DAST.gitlab-ci.yml
# Build stage - compile and test application
build:
stage: build
image: node:18-alpine
script:
- npm ci
- npm run build
- npm run test:unit
artifacts:
paths:
- dist/
expire_in: 1 hour
# SAST - Static Application Security Testing
sast:
stage: security
variables:
SAST_EXCLUDED_PATHS: "spec, test, tests, tmp, node_modules"
SAST_EXCLUDED_ANALYZERS: "eslint"
artifacts:
reports:
sast: gl-sast-report.json
expire_in: 1 week
only:
- merge_requests
- main
- develop
# SCA - Software Composition Analysis (Dependency Scanning)
dependency_scanning:
stage: security
variables:
DS_EXCLUDED_PATHS: "spec, test, tests, tmp"
artifacts:
reports:
dependency_scanning: gl-dependency-scanning-report.json
expire_in: 1 week
only:
- merge_requests
- main
- develop
# DAST - Dynamic Application Security Testing
dast:
stage: security
variables:
DAST_FULL_SCAN_ENABLED: "true"
DAST_AUTH_URL: "https://your-staging-app.com/login"
DAST_USERNAME_FIELD: "email"
DAST_PASSWORD_FIELD: "password"
artifacts:
reports:
dast: gl-dast-report.json
expire_in: 1 week
only:
- schedules
- main
when: manual
# Security gate - fail pipeline on critical vulnerabilities
security_gate:
stage: security
image: alpine:latest
script:
- echo "Evaluating security scan results..."
- echo "Pipeline will fail if critical vulnerabilities are found"
needs:
- sast
- dependency_scanning
only:
- merge_requests
- main
Actions Alternative Template
For teams using GitHub Actions, this equivalent template provides the same security scanning progression with native GitHub integrations:
# .github/workflows/devsecops.yml
name: DevSecOps Pipeline
on:
push:
branches: [ main, develop ]
pull_request:
branches: [ main ]
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v4
- uses: actions/setup-node@v4
with:
node-version: '20'
- run: npm ci
- run: npm run test
- name: SonarCloud SAST Scan
uses: SonarSource/sonarcloud-github-action@master
env:
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
SONAR_TOKEN: ${{ secrets.SONAR_TOKEN }}
sca:
runs-on: ubuntu-latest
needs: build
steps:
- uses: actions/checkout@v4
- name: Run Snyk SCA
uses: snyk/actions/node@master
env:
SNYK_TOKEN: ${{ secrets.SNYK_TOKEN }}
dast:
runs-on: ubuntu-latest
needs: sca
steps:
- uses: actions/checkout@v4
- name: OWASP ZAP DAST Scan
uses: zaproxy/action-full-scan@v0.8.0
with:
target: 'https://example.com'
Key Configuration Points
Security Scan Progression: The template implements a logical flow where SAST analyzes source code first, SCA examines dependencies, and DAST tests the running application. This progression ensures that static vulnerabilities are caught before dynamic testing begins.
Conditional Execution: DAST scans run only on scheduled builds or manual triggers to avoid overwhelming staging environments with frequent security tests. SAST and SCA run on every merge request to provide immediate feedback to developers.
Artifact Management: Security reports are preserved as pipeline artifacts for one week, enabling security teams to review findings and track remediation progress over time.
Quick Template Implementation Guide
- Copy & Update
Copy the GitLab template to your project’s .gitlab-ci.yml file and update the DAST_WEBSITE variable with your staging application URL.
- Configure
Configure required secrets in your GitLab project settings, including any authentication credentials needed for DAST scanning.
- Trigger
Commit the pipeline configuration and create a merge request to trigger your first security scan execution.
Download Complete Template: Access the full DevSecOps pipeline template with additional security tools and advanced configurations at the GitLab DevSecOps Repository. This repository provides modular components that can be customized for specific organizational requirements and expanded with additional security scanning tools.
This template provides immediate value by implementing industry-standard security scanning practices while remaining simple enough for teams new to DevSecOps to understand and maintain.
Key Takeaways
DevSecOps pipeline integrates automated security testing directly into CI/CD workflows, enabling teams to identify vulnerabilities early when they’re cheapest to fix. Therefore, organizations implementing mature DevSecOps practices achieve faster time-to-market while maintaining a robust security posture through continuous monitoring and policy enforcement.
Essential implementation steps include:
- Start with shift-left practices by integrating SAST and secret scanning into developer workflows
- Automate security gates that block deployments containing critical vulnerabilities
- Establish feedback loops that provide actionable security insights to development teams
- Treat security as code through Infrastructure as Code and policy automation
- Extend monitoring into production with runtime protection and continuous threat detection
Success requires gradual implementation, beginning with high-impact tools like GitHub Advanced Security or SonarQube, then expanding to comprehensive toolchains that cover the entire software development lifecycle. Furthermore, cultural transformation proves equally important as technical implementation, and security must become a shared responsibility rather than a separate team function.
Have a project in mind? Contact us to integrate a whole DevSecOps dedicated team into your business. Focus on what matters – scaling profits, fewer headcounts
Frequenty Asked Questions
DevOps pipelines focus on automating software delivery through continuous integration and deployment, while DevSecOps pipelines embed security testing, policy enforcement, and compliance validation throughout every stage of the development lifecycle. DevSecOps transforms security from a final gate into a continuous practice that runs parallel to development activities.
Implement SCA scanning incrementally by starting with critical dependencies only, then expanding coverage gradually. Configure SCA tools to scan during off-peak hours or parallel to other build activities, and cache dependency analysis results to avoid rescanning unchanged components. Tools like Snyk and OWASP Dependency-Check offer fast scanning modes specifically designed for CI/CD integration.
Focus on actionable metrics including mean time to remediation (MTTR) for security vulnerabilities, vulnerability escape rate to production, security test coverage percentage, and false positive rates from automated scanning tools. Additionally, track developer adoption metrics like security tool usage and training completion to ensure cultural transformation supports technical implementation.
DevSecOps complements rather than replaces penetration testing by providing continuous automated security validation throughout development. While DevSecOps catches common vulnerabilities early through SAST, DAST, and SCA scanning, penetration testing remains essential for identifying complex attack scenarios, business logic flaws, and sophisticated threats that automated tools cannot detect.
Most organizations achieve basic DevSecOps capabilities within 3-6 months by implementing foundational tools like SAST scanning and secrets management. However, mature DevSecOps practices including comprehensive monitoring, policy automation, and cultural transformation typically require 12-18 months of sustained effort. Success depends on starting with high-impact, low-friction changes before expanding to comprehensive security coverage.
Establish triage processes that prioritize vulnerabilities based on exploitability, business impact, and environmental context. Configure scanning tools to suppress known false positives and tune detection rules for application-specific contexts. Implement feedback loops where developers can mark false positives, enabling continuous improvement of scanning accuracy over time.
Let’s start with Sunbytes
Let us know your requirements for the team and we will contact you right away.


