Web Application and API Penetration Testing
Protect your business with our comprehensive web application and API penetration testing services.

Web Application Penetration Testing Beyond the OWASP Top 10
While the OWASP Top 10 provides a solid foundation for addressing common web application threats, such as XSS, SQL injection, and broken authentication, it represents only the baseline. Many real-world attacks exploit business logic flaws, chained vulnerabilities, and insecure workflows that fall outside the scope of standard checklists.Key Features That Set Our Services Apart
Our penetration testing goes beyond automated scanning by combining targeted automation with deep manual analysis. We uncover complex, context-aware vulnerabilities such as authentication bypasses, authorization issues, and misuse of application logic, threats that traditional tools often miss. Each finding is thoroughly verified and accompanied by a clear proof of concept and tailored remediation guidance.

We conduct manual penetration testing of web applications and APIs, including REST, GraphQL, and SOAP, supported by custom scripts and tools designed for each asset under assessment. Testing can be performed in black box, grey box, or white box modes, depending on your needs.
This comprehensive approach allows us to identify subtle vulnerabilities in your business logic and operational controls, enhancing your security posture far beyond basic checklist compliance. After the test, you’ll receive detailed findings and actionable recommendations to strengthen the resilience of your web apps and backend APIs against cyber threats.
Manual vs Automated Testing
Automated scanners catch low-hanging fruit. We use automated scanning tools for initial enumeration, typically less than 10% of the engagement. From there, our penetration testers apply deep manual testing techniques that go far beyond what scanners can detect.
Our Process and Methodology
Our web application testing methodology is structured, transparent, and tailored to your environment. Here’s how it works:
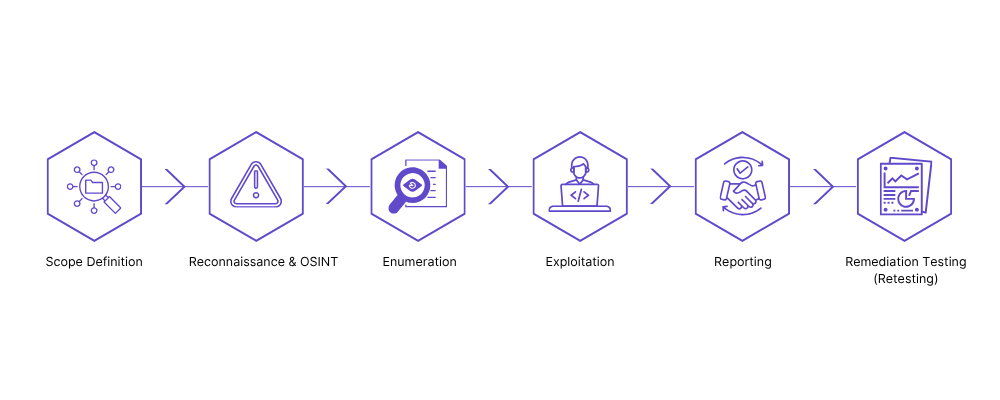

Scope Definition: We collaborate with your team to define clear testing parameters, environments (prod/test), timelines, and emergency contacts. This ensures efficient, low-impact engagement.

Reconnaissance & OSINT: We gather publicly available data, documents, leaked credentials, API keys, domain variants, mimicking what an attacker would see before launching an attack.

Enumeration: We actively map your app using tools like Burp Suite and custom scripts to uncover endpoints, hidden paths, authentication mechanisms, subdomains, third-party services, and technology stacks.

Exploitation: Our consultants manually exploit identified weaknesses in a safe, controlled manner.

Reporting: Executive Summary, Threat modeling & severity scoring (CVSS/NIST), Reproducible Proof-of-Concept, Developer-friendly remediation guidance, and Optional customer-facing summary & attestation letter.

Remediation Testing (Retesting): After fixes are applied, we retest all issues to confirm resolution and ensure no new risks were introduced. You receive an updated report reflecting your improved security posture up to 03 months!
c
FAQ
Manual testing of authentication, sessions, access control, logic, and APIs. It simulates real attacks to find actual impact, unlike basic scans.
Annually, or after major updates. Compliance might require more frequent testing.
Automated tools miss critical logic flaws and dynamic chained vulnerabilities. Manual testing uses human expertise to find what scanners can’t.
3-7 business days for the test itself, with reports and support provided within a week after.
Vulnerability scanning is an automated process that identifies potential weaknesses in systems or applications. Penetration testing goes further by attempting to exploit those vulnerabilities to assess their real-world impact and potential consequences.
contact
Let’s discuss your cybersecurity needs with us
Drop us a line and we’re just 1 click away to make your projects ready