If you’re just starting out safeguarding your business from cyberattacks, it’s essential to grasp these fundamental principles:
You Are a Target – No Business Is Too Small for Cyberattacks
Hackers frequently target small and medium-sized enterprises (SMEs), often viewing them as easier entry points and practice grounds to later move up in rankings. Automated bots continuously scan the internet for vulnerabilities, regardless of a company’s size. If a company stores customer data or handles payment information, it is already a potential target.
Industries such as Government, Healthcare, and Finance are particularly high-risk. In many cases, attackers exploit smaller, less secure businesses as stepping stones in larger supply chain cyberattacks.
And especially, for SMEs, they can go out of business if they do not invest in cybersecurity wisely. Many had been forced out of business and had stopped operation entirely.
Similarly, failing to comply with security regulations in the EU can result in significant financial penalties – GDPR fine tracker.
Read more: The Ultimate Guide to GDPR Audit in 2025
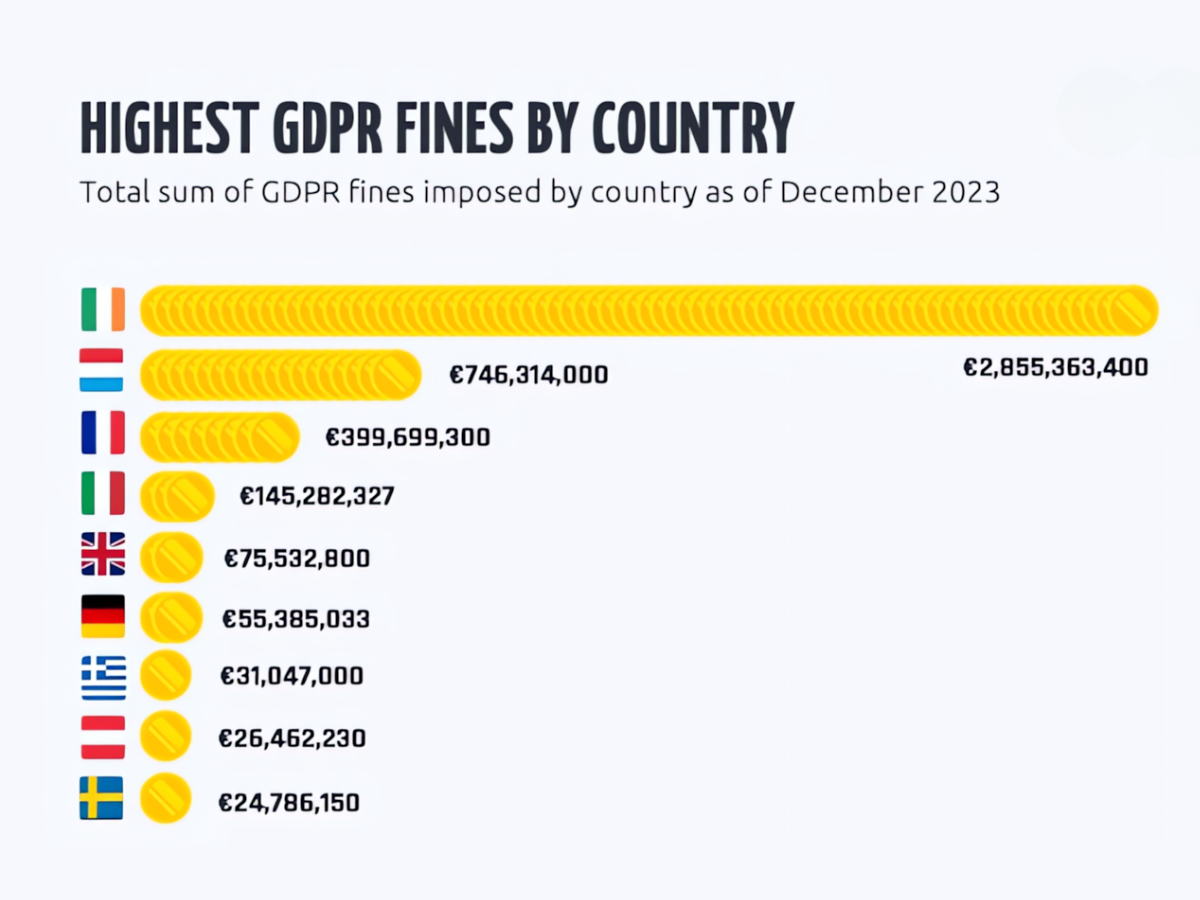
The majority of GDPR fines are issued in Europe
Strong Passwords and Multi-Factor Authentication (MFA) should not be Negotiable
Enforce complex passwords and enable MFA, and remember to remove default credentials across all business accounts. A password manager can simplify this process and improve overall security at minimal to no cost.
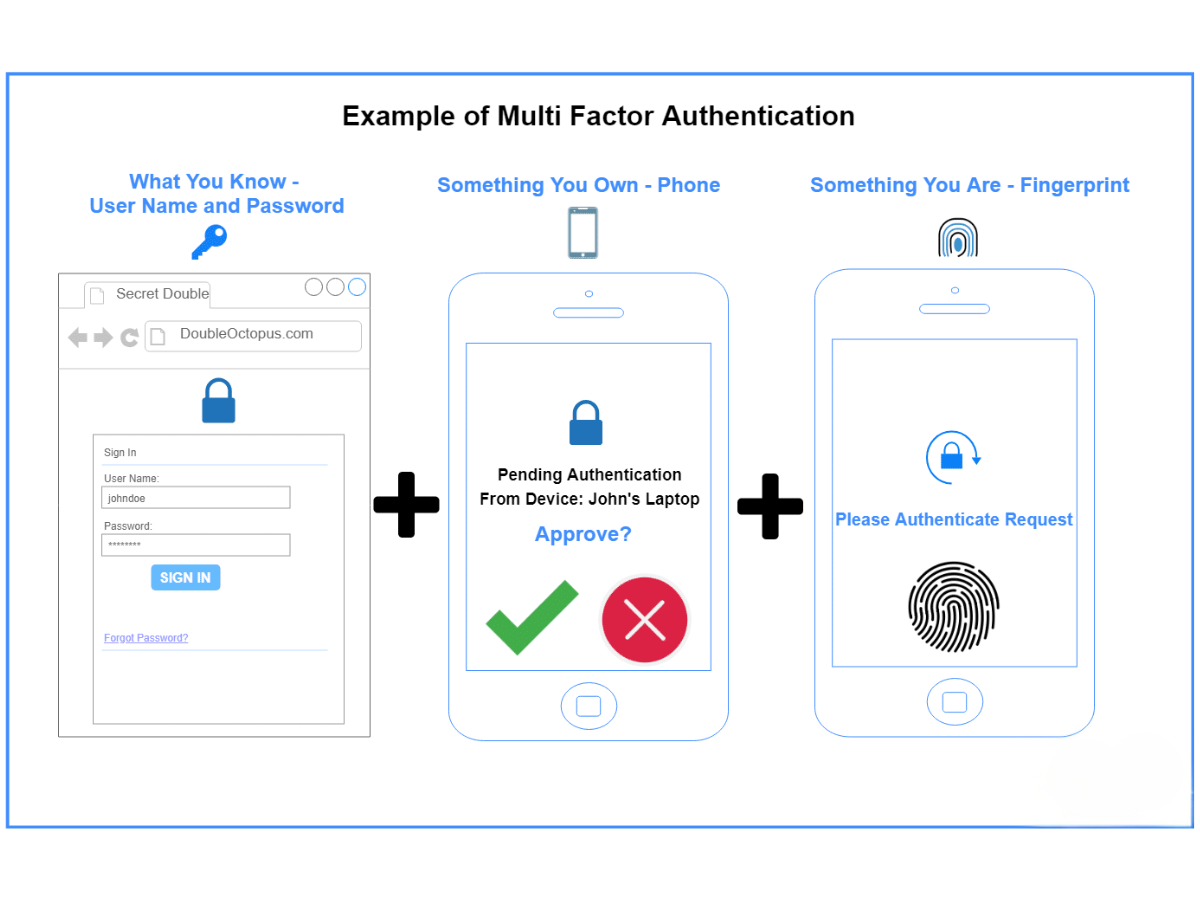
Passwords and Multi-Factor Authentication
Email Is Your Most Common Threat Vector
Phishing remains one of the most prevalent and successful attack methods, accounting for over 80% of cyberattacks. Train all staff, including yourself, to identify suspicious emails. Be cautious of messages that create urgency or offer incentives to click links or download attachments. Take it a step further: run phishing simulations to test your team in real-world scenarios and identify areas for improvement.
Keep Systems and Software Updated
Outdated systems are low-hanging fruit for attackers. Regular patching and updates for operating systems, apps, and plugins can drastically reduce your exposure to known vulnerabilities. Set updates to install automatically wherever possible.
Backups Are the Best Business Insurance
Implement automated, routine backups of all critical data. Follow the 3-2-1 rule:
- Keep three copies of your data
- On two different media types
- With one copy stored offsite or in a separate cloud account
A robust backup strategy is often the deciding factor between successful recovery and catastrophic loss.
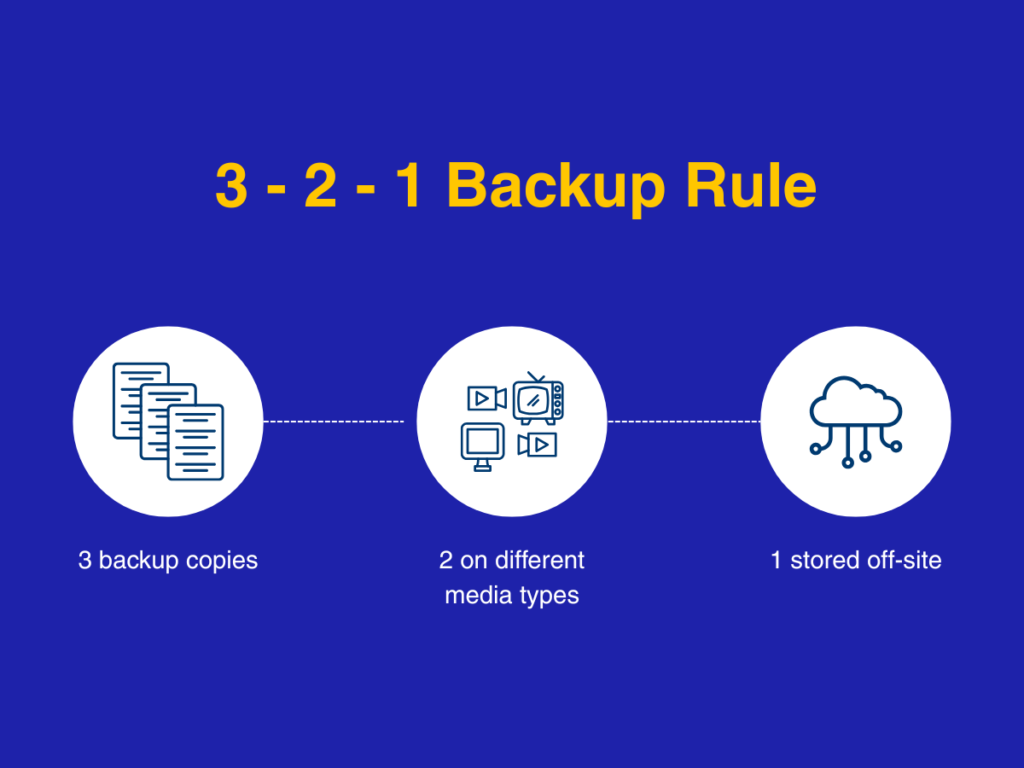
3-2-1 Backup Rule
Use Antivirus Software, Firewalls, and Secure Networks
Basic security tools still matter. Install and maintain reputable antivirus software and firewalls. Protect your Wi-Fi with strong passwords, and segment your network. For example, keep guest access separate from internal systems.
Know When to Seek Experts’ Help
You don’t need to become a cybersecurity expert, but consulting with one can help you efficiently identify and address critical vulnerabilities. That’s where Sunbytes comes in. We offer affordable risk assessments and personalized recommendations tailored to your business’s size and specific needs.

Sunbytes is your trusted security sidekick!
People Are Your First Line of Defense
Human error is the root cause of most cyberattack incidents. Provide ongoing cybersecurity awareness training to all staff. Even short monthly sessions can dramatically reduce risks and improve your overall security posture.

Cybersecurity training for Sunbytes staff
Bonus Tip: Prioritize These 3 Areas First
If you’re overwhelmed, start with these three steps first:
- Set up Single Sign-On (SSO) and protect all business-critical accounts with MFA
- Back up your data using the 3-2-1 rule
- Train your employees with regular phishing simulations and awareness sessions
With proper documentation and commitment, you can measure its return on investment and achieve up to 4x ROI through incident prevention, reduced downtime, and regulatory compliance.
Fear Products – Embrace Process.
Want to take the next step? Contact us to get expert advice tailored for SMEs. We understand the resource constraints you face – that’s why our security solutions are affordable, effective, and built for the long haul.
Let’s start with Sunbytes
Let us know your requirements for the team and we will contact you right away.


